Let us begin our Tor Network review by noting that Tor Browser is a modified version of Mozilla Firefox. What makes it different from other web browsers is that it has been modified by the Tor Project for enhanced anonymity. These modifications have been made to ensure that the browser does not reveal your true IP address when connected to the Tor (The Onion Router) network. Consequently, the browser automatically connects to the Tor network when you open it. It also comes bundled with an add-on called NoScript. NoScript blocks JavaScript security exploits. Although NoScript adds additional security and privacy to your browsing experience, it can break some websites because of its filtering settings.
The Tor Network
Before we look at the Tor Browser, it is necessary to look at the network it is designed to work with, the Tor network. Depending on who you ask, the Tor Network is a tool for privacy that protects those in repressive regimes from reprisal and allows them to report atrocities to the outside world. Others think that it is a tool that hides all sorts of criminal enterprises. Actually, it is both and neither. It is simply a tool which is designed to maximize your anonymity while using the Internet. Although you can use the Tor network to access regular public websites, it can also be used to access hidden services. Hidden services are also called the Dark Web because most are not monitored or given verification certificates.
Accessing Public Internet Sites Using Tor
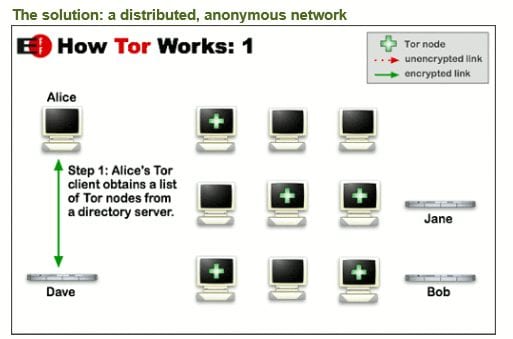
Before we look at how Tor is used to access the Dark Web, we are first going to see how it accesses public websites as shown by the EFF (Electronic Frontier Foundation). The first thing the Tor client does is obtain a list of Tor nodes from a Tor directory server.
Next the Tor client randomly chooses three Tor nodes to create a circuit path to its destination. The data at the client is encrypted using the public keys of the three circuit nodes in reverse order.
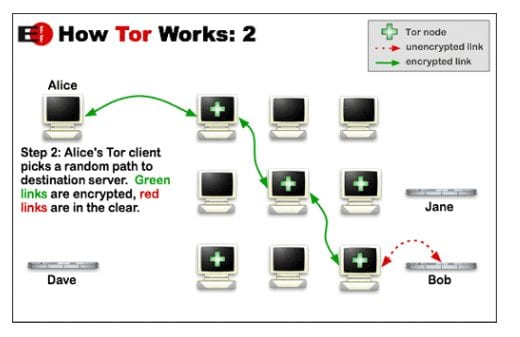
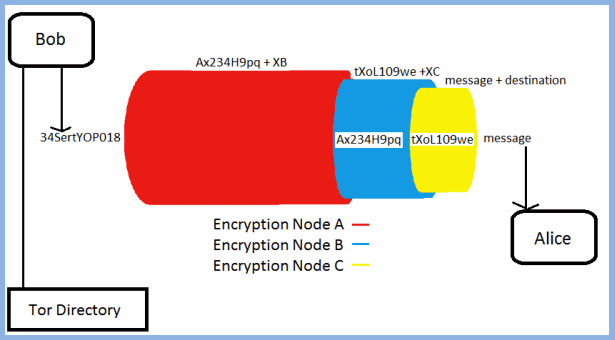
This essentially creates three concentric TSL tunnels to encapsulate your data. To illustrate this, assume that the nodes chosen are labeled A, B, C, and that the site destination is alice.test.net. A is the entry node, B is the middle node, and C is the exit node. The encryption at the Tor client takes place in three stages:
- First, the public key of the exit node C is used to encrypt the message and the site destination. Let us say that this encryption result is tXoL109we.
- Next, the public key of the middle node is used to encrypt the result of the first encryption: tXoL109we and the identifier for node C: XC. This result of this encryption is Ax234H9pq.
- Finally, the public key of node A is used to encrypt Ax234H9pq and the identifier for B: XB. This encryption result is 34SertYOP018.
Decrypting the Message Using Tor
Now that the message has been encrypted using the three circuit node’s public keys, the encrypted message 34SertYOP018, is sent to the entry node A. It uses its private key to decrypt 34SertYOP018 into Ax234H9pq and XB. This strips off the first layer of encryption. It now sends the partially decrypted message: Ax234H9pq to the middle node B using its identifier.
Node B then decrypts Ax234H9pq using its private key into tXoL109we and XC. This strips off the second layer of encryption. It then sends tXoL109we to the exit node C using its identifier.
Finally the exit node C decrypts tXoL109we into the original message and its destination. This strips off the last layer of encryption. The stripping off the encryption by layers is called onion routing and how The Onion Router (Tor) got its name. It then sends the unencrypted message to the destination, alice.test.net. To increase your privacy even more, you should only access sites using the secure encrypted HTTPS protocol so that your unencrypted data is not seen by the ISP or the exit node. You could also take advantage of a trusted VPN service to obfuscate your true IP address from the entry node. However, be aware that this will slow your connection.
Protecting Your Anonymity: Who Knows What?
Now that you have seen how the Tor network operates, let us look at how it makes you anonymous. We can do that by examining what each node knows.
- Node A knows your location and the next destination node B. It does not know either the message or its destination.
- Node B knows only the next destination, node C. It does not know your location, the message, or the final destination.
- Node C knows the message and its final destination but not the location of the sender.
On a public network, a tracker knows both the source and the final destination of your traffic. Therefore, it can develop a profile for your Internet habits and interests. This can even include private health information depending on the sites you visit. However, as you can see, no single node knows the sender location and final destination. Therefore, neither does the tracker. This makes it hard to track what you are doing while using the Tor network. Specifically, this protects you from traffic analysis, a common form of Internet surveillance that depends on knowing both of these.
Using Tor to Access the Dark Web
To understand how Tor clients access the Dark Web, you must first understand hidden services and how they are created using Tor. Hidden services are the backbone of the Dark Web and do not exist outside of Tor. If you have a service that you want to appear on the Dark web there are a few steps that you must do to register it with Tor. Note in this example, Bob is the client and Joe is the hidden service.
- You must choose three nodes and create circuits to them. Once you have created these three circuits, you must ask them to serve as introductory points for your service by sending each your public key. Remember from above that full circuits make it hard for anyone to connect the introductory nodes back to the service IP address.
- Once you have your introductory relays for your service, you must advertise it. You do this by creating a hidden service descriptor which consists of your public key and summaries of your three introductory relays. You sign this with your private key and upload it to a distributed hash table database. Tor clients can then look for this hidden service by using XYZ.onion, where XYZ is a 16 character name derived from its public key.
- After the hidden service is advertised, the client can check the hidden services database to find out more information on it by downloading its descriptor from the distributed hash table database. Remember this descriptor contains its public key and introduction nodes. Simultaneously, the client creates a circuit to a random node to create a rendezvous point for it and the hidden service.
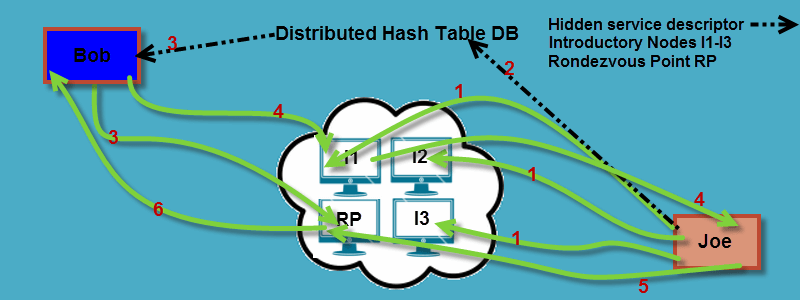
- Once the descriptor info and rendezvous point are on hand, the client creates an introduce message that consists of the address of the rendezvous point and a one time secret and encrypts it using the hidden service public key. It then sends the introduce message to one of the hidden service’s introduction nodes and requests that it be sent to the hidden service.
- The hidden service decrypts the client’s introduction message. The service then creates a circuit to the rendezvous point and sends the one-time secret to it in a rendezvous message.
- The rendezvous point notifies the client of a successful connection to the hidden service.
The client and hidden service can now transfer end-to-end encrypted messages between each other. The rendezvous circuit now consists of six nodes. Three are supplied by the client and three come from the hidden service. This ensures that the client IP address is hidden from the hidden service and vice-versa. When accessing a hidden service, your transactions are hidden from the public Internet because no exit nodes are used.
History of the Tor Project
The idea behind an anonymity network was hatched in the mid 1990s by three United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag. Their goal was to find a way to secure online intelligence traffic. In its early years, the so called onion routing concept went through a few different iterations. Many ideas were tried and then forgotten. Some were revived in the second generation of the Tor project. In 1998, several generation 0/1 onion networks were set up and tested including an independent one in Canada. Also in 1998, A commercial network, the Freedom Network, with similar properties to onion routing was launched but later failed due to lack of interest. Development stalled on the onion network in 1999, when its developers left NRL for other opportunities and funding was cut.
In 2000, Syverson met Dingledine at a privacy workshop and the modern day seeds for Tor development were planted. Onion router development resumed in 2001 with funding from Defense Advanced Research Projects Agency (DARPA). In 2002, development of Tor, an instance of onion routing was designed by Roger Dingledine, Nick Mathewson, and Syverson. In October 2003, the Tor network was deployed and its code was released under the free and open MIT license. It is a small network with about a dozen nodes. By the end of 2004, EFF began funding for the Tor development and hidden services were deployed when the hidden wiki was created. This innocent action was the beginning of the so-called Dark Web. By 2005, the Tor network had expanded to 160 nodes on five different continents.
In December 2006, Dingledine, Mathewson, and five others founded the current Tor Project, a 501 (c) non-profit organization responsible for maintaining Tor. The EFF acted as its primary financial sponsor with additional funding by the Human Rights Watch, Google, the University of Cambridge, and others. The Tor project is still responsible for monitoring and maintaining the Tor network today. This includes new programming to fix bugs and guard against attack exploits against the network. Primary funding is through the US government. In 2016 the entire Tor Project board resigned and installed a new board which includes Cindy Cohn, Executive Director, Electronic Frontier Foundation (EFF); Gabriella Coleman, an anthropologist at McGill University and a sociologist; Megan Price, Executive Director, Human Rights Data Analysis Group; Matt Blaze, University of Pennsylvania associate professor and cryptographer; Bruce Schneier, security expert and author; and Linus Nordberg, Tor programmer. This was to provide a more diversified board to usher the Tor Project into the future. Former board members Dingledine and Mathewson continue with the Tor Project as leaders of its technical research and development department.
Who Uses the Tor Network
You may have heard that the Dark Web is a cesspool of criminal activities that is part of the Tor network. While this may be part of the story, it is a very incomplete one. A variety of people and organizations use Tor to maintain both their anonymity and that of their clients. These include the following:
- Normal people – They use the Tor network to protect themselves from traffic analysis, avoid incessant targeted marketing, skirt unwanted Internet surveillance, and to research sensitive topics or circumvent censorship if they reside in a country with a national firewall.
- Journalists – Citizens and journalists across the world use the Tor network to research state propaganda, file stories with non-state controlled media and authorities, and avoid the repercussions that their Internet curiosity might invite in countries like China, Iran, Russia, Turkey, and others. This allows them and their audiences to cover controversial topics like government corruption, religion, democracy and others with a decreased fear of reprisals.
- Law enforcement – A variety of government agencies and law enforcement groups use the Tor network to conduct Internet surveillance, undercover sting operations without leaving government IPs in the usage logs. It can also allow anonymous tipsters to be more comfortable that their anonymity will be maintained as law enforcement does not know who they are and thus can not be compelled to reveal their identities.
- Activists and Whistleblowers – Human rights activists can use Tor to report on abuses from dangerous areas. Even in the US, activists have over time been unjustly surveilled. This has increased since new Homeland Security rules were implemented. Whistleblowers everywhere can use the anonymity provided by Tor to avoid reprisals from companies, individuals, or governments. Sometimes this can even save their lives. The Supreme Court has removed legal protections from government whistleblowers. Tor allows them to get some of this protection back through anonymity.
- Professionals – High profile people use the Tor network to state controversial opinions they might have without it affecting their professional life.
- The voiceless masses – People living with the fiscal help of government entities are often afraid to voice grievances they have with these systems for fear of the fact that every thing that they say on the Internet is recorded for prosperity and could come back to bite them in the future.
- Business leaders – They use the Tor network to protect company strategies that could be revealed by Internet research that they conduct and to anonymously keep tabs on their competitors.
- Military – Military services use it to protect field agents, mask command and control facilities, and to gather anonymous intelligence from insurgent sites.
- IT professionals – Network administrators and other IT people use Tor to test their network security, deploy services without needing extra equipment, and work around other issues such as DNS problems.
This is just a smattering of the legitimate Tor uses. As you can see, all kinds of people utilize the Tor network for a variety of reasons but all have one main goal: to increase their anonymity while using the Internet. Legitimate organizations like Facebook – http://facebookcorewwwi.onion/ – , The Hidden Wiki – http://kpvz7ki2v5agwt35.onion/, DuckDuckGo search engine – http://3g2upl4pq6kufc4m.onion/, and others create these services for use by people in the US, as well as users in less democratic countries. These mirrored Dark Web services allow individuals to have places where they can display their grievances, conduct research, and perform anonymous searches. Hidden services on the Dark Web cover as large a gambit of roles as there are people that use them.
Finally, yes criminals have also set up shop on the Tor network selling everything from illicit drugs, illegal pornography, stolen identities, to outright murder. There are Dark Web sites that exists to scam unsuspecting users. Fraud is rampant among the criminal services. Hate groups have recently retreated to the anonymity of the Dark Web as they have been ostracized from legitimate sites like Facebook, Twitter and others. Anarchists and other radical ideologies protect their anonymity using it. Consequently, users of the Dark Web should be aware of this and only visit sites that they know and have some degree of trust in.
Does Tor Keep You Absolutely Anonymous?
To answer this question, we have to look at the case of Silk Road, the first highly successful black marketplace on the Dark Web. This has been followed by several other high profile law enforcement takedowns of hidden services on the Dark Web. Another thing to note is that it took the entire resources of the United States law enforcement and Europol to achieve these takedowns.
As to whether Tor can keep you absolutely anonymous. The answer is no, but it does not claim to. It simply claims to help you be more anonymous while using the Internet. As these cases will show, whether you stay anonymous when using Tor services can also depend on your actions as we will see when we look at the Tor Browser itself.
Dread Pirate Roberts and the Silk Road
Silk Road started as a young libertarian’s anonymous marketplace experiment where vendors and users could meet to buy and sell illicit drugs. Like many young people of his generation, he felt that drug use should be a personal choice without government interference. From its start in January of 2011 when he sold home grown mushrooms, it was an instant success with more vendors and users joining every day. Silk Road was stylized after popular Internet markets like eBay and Amazon which deliver though regular postal channels.
Its anonymous administrator created a strict code of conduct for his site, “No child porn, stolen goods, or fake degrees.” He summed it up like so: “Our basic rules are to treat others as you would wish to be treated and don’t do anything to hurt or scam someone else.” By 2012, Silk Road and its administrator had become a voice for individual liberty, both on the Internet and in real life. This led him to take the pseudonym Dread Pirate Roberts or DPR for short so he could espouse his libertarian ideology and ignited a cult following for both Silk Road and its administrator, DPR. As Silk Road expanded globally, the man behind DPR became comfortable with his role as a libertarian leader. He offered his users hugs and drugs as fitting his Eastern inspired philosophy. Unfortunately, it also brought him and his site to the attention of law enforcement.
Although various law enforcement agencies examined Silk Road in mid-2011, they got nowhere. As the site gained popularity, more shipments began to be discovered by postal authorities. In early 2012 Homeland Security assembled a task force to investigate Silk Road and see if they could figure out the man behind the mystique of Dread Pirate Roberts. By 2013, Silk Road had investigations from Homeland Security, FBI, DEA, IRS and the US Postal Service. This made the hunt for DPR the largest cyber manhunt in history and the agency that broke it would have bragging rights.
After two years of almost no progress, the cybercrime unit of the FBI which had been throwing data at Silk Road and looking for IP address leaks that could help then de-anonymize the site got a break when one of the IPs they tried returned a page from the Silk Road site. DPR had supposedly been warned that his site might be leaking but ignored these warnings because he was over confident in his anonymity. They had the location of the hidden Silk Road server which led them to the secure Thor Data Center in Iceland. With cooperation from the Iceland authorities they were able to obtain the mirror drive for the site. Finally, they literally had Silk Road in their hands and were one step closer to DPR.
To complicate matters for DPR, the data center kept site logs for six months so they could see all the IPs that had recently connected to it. Forensic cyber analysis of the drive and logs led to several non-Tor addresses that had used port 22, the SSH connection that admins used. They identified these as a backup in Philadelphia, a hosting proxy server in France, and a VPN in Romania. Mapping these connections led them to an IP address that was the last known login to the Silk Road. Some further investigation gave its location as Café Luna, Sacramento Street, San Francisco. They now knew where to look for DPR.
A series of events eventually led to DPR’s downfall once the agencies started sharing information from their investigations. If these agencies had not all been investigating DPR at the same time, he likely would not have been caught.
- The FBI had recreated Silk Road at their New York cybercrime offices where they had super-user rights and could examine all of its features and code. The chart they created from this showed the IP address with the name Frosty and the ID of the Iceland box. Cross-referencing this with other evidence, they discovered that the Silk Road servers had a login system that created one trusted machine for all others , whose encryption keys all ended in frosty@frosty.
- Homeland Security had found some fake IDs with the name Ross Ulbricht on them at the Canadian border. They had come to his San Francisco home in Café Luna (the site where an administrator had logged into the Silk Road VPN), questioned him about them, and made a report.
- An IRS agent had discovered that about the same time that Silk Road surfaced, someone named Altoid was talking it up on a forum. A subsequent Google search of Altoid revealed a question in 2013 about connecting to a Tor hidden service using curl in PHP, with the listed email address rossulbricht@gmail.com. A minute later the user changed his alias to Frosty.
After all of this was discovered, they started on-site observation of Ulbricht to correlate his laptop usage with DPR administrative logins to Silk Road. Once they were sure they had enough statistical timing data to be sure that this was indeed DPR, the elusive administrator of Silk Road, they set about trying to get his laptop while he was logged in to seal their case. They were able to do this despite problems with their original plan.
They could see everything. The machine ID was Frosty. Ross was logged in to Silk Road as an administrator under an account called /Mastermind. The FBI now had full control of the Silk Road site. Thereafter, the Silk Road welcome page read: THIS HIDDEN SITE HAS BEEN SEIZED BY THE FEDERAL BUREAU OF INVESTIGATION. Ross Ulbricht was convicted of all seven counts against him and sentenced to life in prison. An appellate court upheld his conviction and sentence on May 31, 2017, closing the Silk Road case.
Operation Onymous
November 5-6, 2014, a number of websites were shut down in a joint operation between US and European law enforcement. Seventeen people were arrested. The government claimed initially that over 400 sites had been shut down. They later amended this to over 50. Most people think the number of actual sites was about 27 which were associated to about 414 onion addresses. The sites included Silk Road 2, Cloud 9 and Hydra. Silk Road 2 was their primary target and Blake Benthall, a 26-year old software developer was named as its administrator Defcon.
Authorities say that a number of mistakes by Benthall: including using his personal credit cards and email address, giving away his location on social media, and making huge purchases with Bitcoin from illicit sources, led to his arrest and indirectly to others. Also shut down were contraband markets like Pandora, Blue Sky, Topix, Flugsvamp, Cannabis Road, and Black Market. Money laundering sites like Cash Machine, Cash Flow, Golden Nugget and Fast Cash were removed. The scope of the operation made many wonder if the government had used an unknown exploit to de-anonymize these Tor sites. Even today, no one knows the real story of how Operation Onymous was implemented because it is widely believed the authorities use made up scenarios to cover their real actions in these cyber takedowns.
Alphabay and Hansa
In July of 2017, US Department of Justice and Europol announced the closure of Alphabay, the world’s largest Dark Web market with estimated sales of over a billion dollars. Simultaneously, Dutch authorities announced the take down of Hansa, another black market site. As in previous cases, the government was mum as to how they found the location of these hidden services.
The Tor Browser
By now, you can see that using the Tor network would be hard for most people if tools like the Tor anonymizing browser did not exist. Its main benefit is that it makes it easy for those with limited technical knowledge to take advantage of the anonymity provided by the Tor network. It has been modified to provide the best anonymity available without requiring user adjustments. The Tor browser is bundled with other anonymity add-ons like HTTPS Everywhere and No-Script. It defaults to the anonymous search engine DuckDuckGo to increase your anonymity even more.
Installing the Tor Browser Bundle
The Tor Browser will allow you to use Tor on Microsoft Windows, Mac OS X, or GNU/Linux without additional software. Because of this, it can run directly from your computer or off a USB flash drive. After you download the proper Tor Browser bundle for your OS from their website, you can install it on your computer or a thumb drive. Installing it on a flash drive will allow you to use it on different machines without having to install it on each.
Run the downloaded file as administrator to begin the Tor Browser installation process on your chosen device. Choose your language and select the “OK” button to continue. On the next screen, select the default setup directory and click the “Install” button. After setup completes, choose your startup options and then hit the “Finish” button.
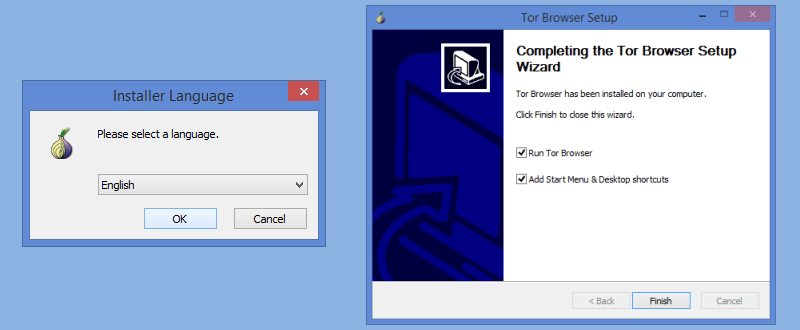
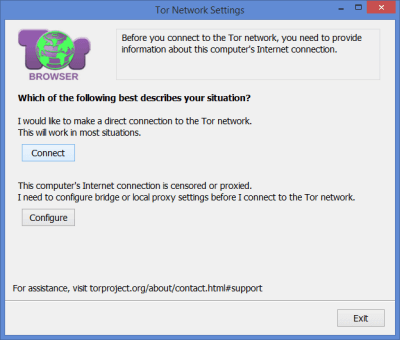
You will then see the Tor network settings screen. This screen has two options for connecting to the Tor network. Most users will choose to connect directly to the Tor network and therefore will require no extra setup. However, if Tor is being censored by your ISP or if you need to configure a proxy to the Internet, then you will need to select the “Configure” button.
This will bring up a screen that will create a bridge connection to the Tor network. This is designed to hide your connection to Tor so that the connection will not be blocked. More sophisticated censoring techniques like Deep Packet Inspection (DPI) used by some countries can sometimes detect Tor connections despite using a bridge. To combat this Tor uses plugable transports. These manipulate all Tor traffic between the client and its first hop so that it cannot be identified as Tor traffic. Occasionally, even these are discovered and replaced. The current safe transports are obfs3, fte, meek-amazon, meek-azure, and obfs4. If you have a different bridge, you can manually enter it. Bridges can be obtained through email from Tor.
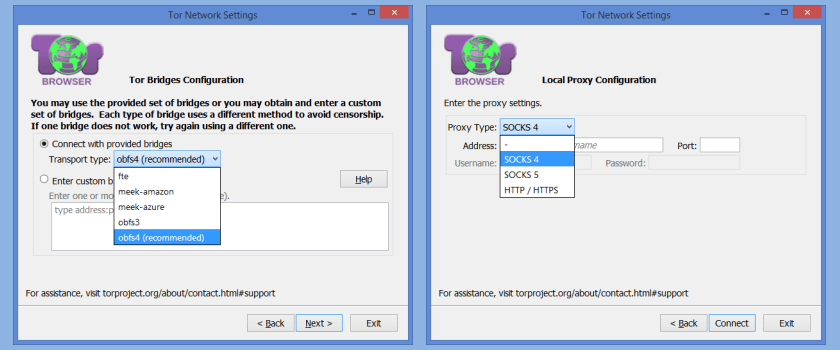 If you have a local proxy configuration, the connection can also be set up to use it. Simply enter the type of proxy (Socks 4, Socks 5, or Https/Http), the IP address, and the port. If you need a username and password, you can also enter these. Finally, click the “Connect” button to finish the setup and open the Tor Browser. These settings will be remembered for future browser use but you can change them if necessary.
If you have a local proxy configuration, the connection can also be set up to use it. Simply enter the type of proxy (Socks 4, Socks 5, or Https/Http), the IP address, and the port. If you need a username and password, you can also enter these. Finally, click the “Connect” button to finish the setup and open the Tor Browser. These settings will be remembered for future browser use but you can change them if necessary.
Using the Tor Browser
The Tor network can hide your location and IP address from interested parties. However, it can not keep third party trackers from creating a profile of your browser activity, at least in the short term. It should be noted that it can make it harder depending on the number of users on that exit server. This is because the statistics generated from this type of software looks at the IP address being used by the browser which is that of the Tor exit node. This rotates about every ten minutes when using the Tor network.
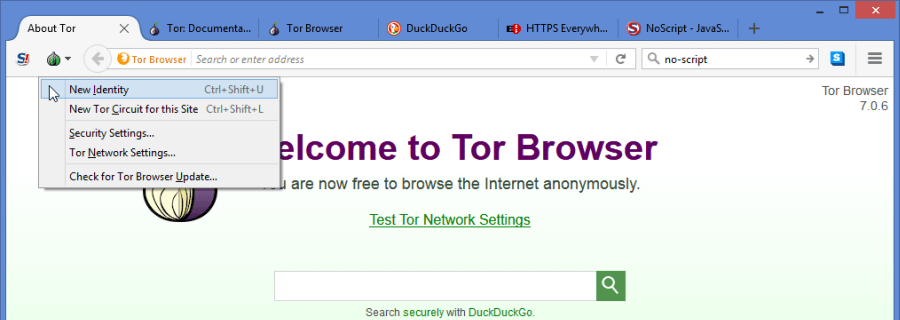
Let us examine the Tor Browser menu to see how it keeps third-party services: social networking “Like” buttons, analytics trackers, and advertising beacons, from linking your browser activity across different sites. Selecting the TorButton (onion icon) displays this menu which consists of the following items:
- New identity – An identity contains all private information for the current session. This includes all cookies, session browsing history, and the Tor circuits created during this session. A new session is created each time you open the Tor Browser. If you select this option, it will delete all information for the current identity, stop all downloads, and close all open sites.
- New Tor circuit for this site – This will reload the current site and all pages associated with it. It will not clear the private information for the current session or stop activities and connections to other open sites.
- Security settings – The default for this is “Low” which enables all browser features. This can also be set to “medium” or “high”. Raising it incrementally disables browser features. You can find more specifics about this in the Tor Browser manual.
- Tor network settings – These are the same settings that we looked at earlier for connecting using a bridge or proxy.
- Check for updates – You should periodically look for new updates.
Now that we have looked at the Tor Browser menu and learned about session identities, let us look at how it uses this to stop browser profiling. When you connect to a website the TorButton will display the circuit used to connect to it, as well as, the menu as shown in the next image. If you look closely, you will see that the top two tabs are two pages from the same site (torproject.com) and that the Tor circuit is the same for both pages. This illustrates that the same Tor circuit is used for all pages of the same site.
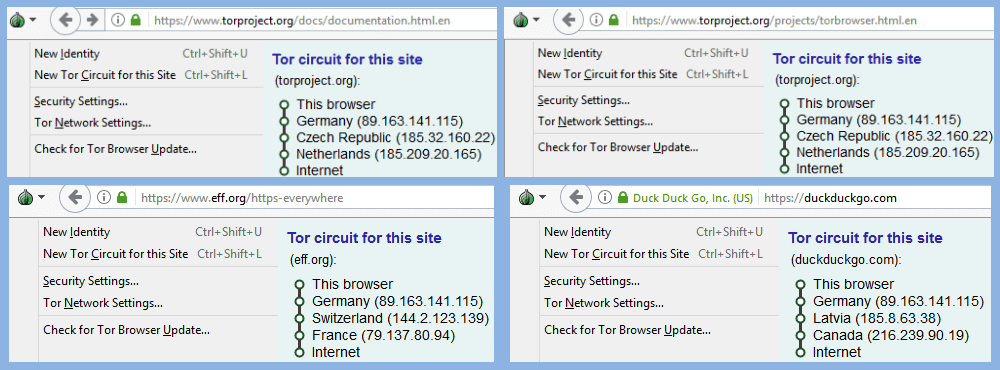
However if you look at the two bottom tabs, you will see that one is for the eff.org site and the other is for the duckduckgo.com site. You can see that The Tor circuits are different for each. This is because Tor Browser uses a new Tor circuit for each new site that is opened in a session. This means that if the same tracker software is installed on different sites, it will see the browser as logging in from a different IP address on each site. Thus, it will be nearly impossible for it to create a profile of your online activities. This is why the Tor Browser can keep you more anonymous than other browsers even if you are using the Tor network with them.
Keeping Your Anonymity While Using Tor Browser
To increase your anonymity while using the Tor Browser, you can use NoScript to determine how you treat Java scripts from different websites. The default is to accept scripts from all sites but we recommend that you change this and only allow them from trusted HTTPS sites. You can do this under the menu item “Options”. You can also whitelist sites to allow Java. The Tor browser also offers you a chance to unlock it one time for some sites that you visit. Adjusting No-Scripts can be tedious as some settings can break sites.
You should also set the Tor Browser to always use HTTPS to make connections using the EFF add-on HTTPS Everywhere as shown below.
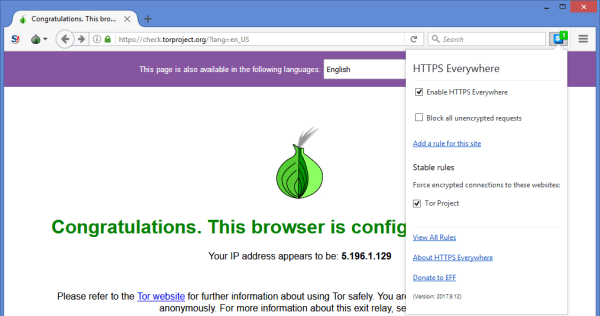
There are a few other things that will help you stay anonymous while using Tor Browser. They include the following:
- Do not torrent over Tor – Tor uses the TCP protocol and most torrent software uses UDP for speed. Some torrent file-sharing applications will therefore ignore proxy settings and make direct connections without using Tor. Also, even if your torrent application connects only through Tor, it may also send out your real IP address in the tracker GET request, because that’s how torrents work. If it does this, it will not only de-anonymize your torrent traffic but also the Tor web traffic as well.
- Do not install additional Firefox plug-ins – Tor Browser will automatically block browser plugins such as Flash, RealPlayer, Quicktime, and others because they can be tricked into revealing your true IP address. Other plug-ins may do the same so it is better not to install them on the Tor Browser.
- Don’t open documents downloaded through Tor while online – Some documents that you download have Internet elements in them which will open outside of Tor and compromise your anonymity. The Tor Browser will warn you about this. Do not ignore this warning.
- Do not fill in forms – Avoid filling in forms with your personal information while using the Tor Browser. Also, using Tor Browser will show you in places you normally are not in and banks and other institutions may want to verify who you are before they let you log in.
If you follow these simple guidelines when using the Tor Browser, your anonymity should not be compromised.
Tor Network & Browser Review : Conclusion
The Tor Browser is a Firefox browser which has been modified by the Tor Project to optimize its anonymity while using the Tor Network. It can be used with Microsoft Windows, Mac OS X, or GNU/Linux without additional software. It can also be installed on a USB flash drive so that you can use it on multiple computers. Using it can help even those with little technical knowledge take advantage of the anonymity provided by using the Tor network.
Using Tor Browser will make you more anonymous than other browsers and can help you avoid profiling by tracking software that is deployed on most sites today. It creates separate Tor circuits to each site that you open while using it. This helps hide your current location from the site and tracking software will not be able to correlate your browser movements either. Thus it can help to keep you more anonymous that other browsers.
Things we like about the Tor Browser
- It makes it easy for anyone to use the Tor Network.
- It makes you more anonymous that other browsers.
Things that we think could be improved.
- Internet speeds are quite slow when connected to the Tor network.
- Some websites block Tor addresses.
However, if anonymity is important to you while using the Internet, the Tor browser it is one of the best solutions available today.