This is our review of Silent Circle which touts itself as an enterprise privacy platform. It sells not only an encrypted communications service, but the hardware, software, and technology necessary to implement it. Recent additions to their platform include the Silent Store, Silent Meetings, Silent Manager, and the rebranded Silent World (formerly Out-of-Circle Calling). The Silent Circle team is a unique mix of world-renowned cryptographers, Silicon Valley software engineers, VoIP engineers, system analysts, and former US Navy SEALs & British Special Air Service (SAS) security experts. They state, ” Silent Circle’s Enterprise Privacy Platform was built upon the company’s original founding purpose: to offer privacy in the face of widespread data surveillance and collection.” Their ultimate goal is to let users conduct business without fear of having their communications hijacked by competitors, governments, or other malicious sources.
Silent Circle started in 2011 when Mike Janke, a former Navy SEAL and security specialist joined forces with Phil Zimmermann, a cryptography expert, and Jon Callas, a computer security engineer and programmer to create an encrypted communications service with easy-to-use tools available to anyone who appreciates a little control over who has access to their conversations. Silent Circle officially launched its secure communications service in October 2012. The original software app was simple to setup and use. You simply installed the apps (Silent Phone, Silent Text, Silent Eyes, and Silent Mail) on any smartphone or tablet and dialed, texted, or sent video or email. Thereafter, any communication was encrypted in a way that neither governments, hackers, or government-backed hackers could break.
On August 8, 2013, the US government ordered encrryted email provider Lavabit to turn over its Secure Sockets Layer (SSL) private keys. Lavabit owner, Ladar Levison shut down his service rather than “become complicit in crimes against the American people” by allowing the NSA to spy on his customers. An example of Silent Circle’s commitment to privacy came just hours later. They explained that email services need to interoperate with other email providers. That makes end-to-end encryption impractical and creates a danger that the company could be compelled to hand over information to the government. Email as we know it with SMTP, POP3, and IMAP cannot be secure. Although they had not yet been told to provide data to the government, they saw the writing on the wall. Consequently, Silent Circle informed customers that it had killed off Silent Mail rather than risk their privacy. They made the decision therefore to remove employee data from the servers and immediately completely wipe them.
In October of 2013, Lavabit founder Ladar Levison and Silent Circle started the Dark Mail initiative to develop a secure end-to-end encrypted protocol and service. Ladar Levison, Dark Mail project lead, dedicated the project to the NSA when he released the Dark Internet Mail Environment – Architecture and Specification in March of this year. His dedication follows:

Silent Circle Hardware
In January 2014, SGP Technologies, a co-venture between Silent Circle and GeeksPhone designed a new model of smartphone called Blackphone. Designed in the wake of Edward Snowden’s 2013 mass surveillance revelations, the Android-based device was said to be “the first NSA-proof” smartphone. The original Blackphone which launched in June of 2014 has the following specifications:
- OS platform PrivatOS based on Android 4.4 (KitKat)
- Screen 4.7″ IPS HD display (1280*720) with pulse-width modulation (PWD) for screen dimming
- Touch Capacitive >4 point multi-touch
- Camera 8MP AF rear (Flash LED) + 5MP FF front
- SIM slot Single micro-SIM slot
- Bluetooth 4.0 LE
- Wi-Fi 802.11b/g/n
- MicroSD support Yes, up to 128GB microSDXC
- Connectors 3.5mm audio jack (TRRS:CTIA/AHJ), micro USB
- Battery capacity 2000 mAh lithium polymer (user replaceable)
The Blackphone today uses a modified version of the Android OS, now called PrivatOS 1.1 or Silent OS which has been designed with security and privacy in mind. It also includes their privacy apps along with some 3rd party privacy apps that have been preinstalled. It provides private web browsing by default, a VPN which prevents eavesdropping over cellular networks, and private cloud storage for files. Features include private encrypted voice and video calls and text messaging with attachments, the Kismet Smarter Wi-Fi Manager which prevents wi-fi hotspots from capturing information or tracking users’ locations or activities, and a comprehensive security center and remote wipe and protect functionality. The new PrivatOS 1.1 also includes Spaces which allows the user to create up to four virtual phones. The Blackphone was named one of Time Magazine’s top 25 inventions of 2014. The Blackphone is sold unlocked and will work with any compatible GSM carrier and will not work with CDMA carriers. In the US GSM carriers include T-Mobile and AT&T but not Verizon or Sprint.
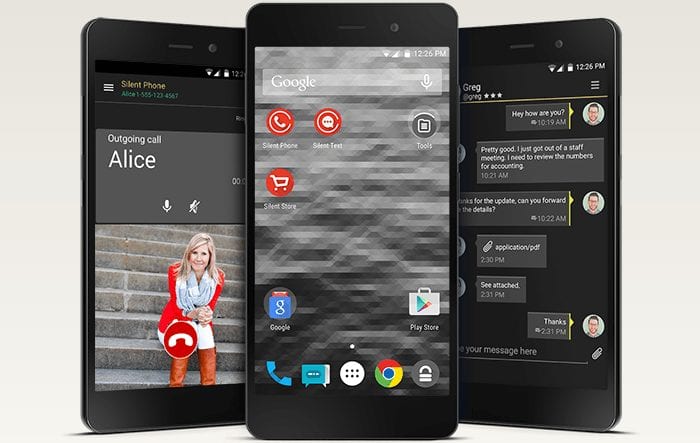
Silent Circle will be releasing their next generation privacy phone, Blackphone 2 in September of 2015. It has the following specifications:
- LTE and Worldwide 3G/HSPA+ connectivity
- 5.5″ FullHD Gorilla Glass display; Resolution 720p (1280 x 720 pixels) to 1080p (1920 x 1080 pixels).
- 1.7 GHz Qualcomm Snapdragon Octa-Core Processor
- 3GB RAM & 32GB internal storage
- microSD card slot supports additional 128GB
- 13 MP BSI Camera Sensor (5 MP front)
- 3060 mAh Battery with Quick Charge 2
As you can see the Blackphone 2 has had quite an upgrade in hardware from its predecessor. In addition to having Silent OS 2.0 and the Silent Suite of software, the new phone will offer the much requested Google services. Therefore, you will now get all the same Google apps that Android users are familiar with like Chrome, YouTube, Maps, and the Google Play store. The integration of the Google services into their Spaces technology shows that Silent Circle is dedicated to combining technical capabilities with ease of use for their customers. As with previous versions of Silent Circle products, every app installed (including those downloaded through the Play Store) is monitored by the Security Center and will only have access to the data that you agree to share so you do not have to compromise your privacy or security. No price has yet been released for the Blackphone 2 but its expected to be about the same as the original.
The new Blackphone 2 also makes it easier for enterprises to integrate it with existing enterprise mobility management (EMM)/mobile device management (MDM) solutions like Citrix, Soti and Good Technology by providing out of the box access to widely used productivity apps. Furthermore, their continued commitment to the Android for Work provides even more features that can be leveraged both by employees and their IT departments. This allows enterprises to increase their productivity and ensure a smooth transition when switching devices.
Silent Circle Software
The original PrivatOS was an Android-based operating system that was created by Silent Circle to address modern privacy concerns. It had no bloatware, no hooks to carriers, and no leaky data. It was the first OS specifically designed to put privacy in the hands of mobile users without sacrificing their productivity.
Recently, PrivatOS 1.1 or Silent OS the first major upgrade to their OS was released. At the heart of their new upgrade are Spaces and Security Center. Together these form an OS-level virtualization and management solution which puts privacy settings at the user’s fingertips. This allows Blackphone and new Blackphone 2 users to control all aspects of their mobile life, personal and professional. Geared specifically for the enterprise, it allows users to keep enterprise and personal apps completely separate from each other.
Spaces allows users to create multiple, separate virtual phones on one device. This lets them keep their personal and professional life securely compartmentalized. Spaces has the following features:
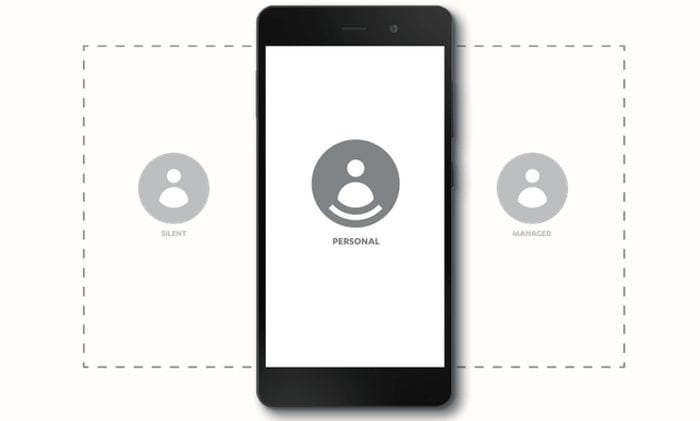
- Create – create up to four separate spaces that act like virtual phones on your device; enterprise, personal, gaming, etc.
- Each Space consumes about 70MB of additional memory when running
- Each new Space requires approximately 3MB of additional storage
- When apps are shared across Spaces, then there is no additional app storage needed beyond the initial copy
- Each app may consume additional app data storage in each Space
- Customize – each space can be customized any way you like; different lockscreens, apps, homescreens, security settings, etc.
- Secure – keeps your apps and data secure
- Spaces are isolated from each using Android and Linux process isolation technologies (containers and SE Android) so that apps and data in one Space cannot gain access to the apps and data in another Space
- The file system for Managed Spaces is encrypted and other Android capabilities such as debugging can be disabled to prevent off-line or recovery partition based attacks in the event your device is lost or stolen
- Data – no data is shared between spaces; shared apps between spaces have independent data
- Enterprise – capacity for IT administrators to create, lock, administer, and wipe enterprise managed spaces.
- Integration – Partnerships with MDM solution providers like Citrix, Soti, and Good Technology
The second major part of the Silent OS is the Security Center which lets users control all their privacy settings with just a few taps. Security Center has the following features:
- Configure – users can easily configure settings for individual spaces
- Manage – users can determine which apps live in each space
- Fine tune – set individual app permissions which allows the user to control the level of data access each app receives
The Blackphone also comes preinstalled with Silent Suite, Silent Circle’s core set of applications that enable private, encrypted communication. It provides peer-to-peer key negotiation, verification, and management. Silent Suite sets the standard for secure mobile communication and can be installed on PrivatOS (Blackphone), as well as, standard iOS and Android devices. Silent Suite consists of the following:

- Silent Phone – allows users to make private voice and video calls in HD clarity over 3G/4G and WiFi networks
- Peer-to-peer encrypted VoIP service (secure Skype functionality)
- It is an easy-to-use app that works using the ZRTP encryption protocol
- Silent Text – an unlimited encrypted text service with the capability to transfer files
- Only supported between other Silent Text users
- Silent Text also offers secure file transfers of up to 100MB and voice memo functionality.
- Burn Notice provides the functionality to destroy selected messages automatically after a preset period of time.
- SCIMP is the Silent Circle Instant Message Protocol which makes Silent Text’s secure device-to-device texting possible
- Peer-to-peer encryption keys stay on the device and not on the Silent Network servers so only you and the person you are texting can decrypt and read the information.
- The Secure Authentication String (SAS) for each text is unique and used only once which provides forward secrecy
- Silent Contacts – An automatically encrypted address book
- Password protect the encrypted address book to lock it so that only you can access it
- Import and encrypt your existing contacts from other sources.
In November 2014, Silent Phone and Silent Text both received top scores (7/7) on the Electronic Frontier Foundation’s secure messaging scorecard. They received points for having communications encrypted in transit, having end-to-end encryption, making it possible for users to independently verify their correspondent’s identities, supporting forward secrecy, having their code open to independent review, having their security designs well-documented, and having recent independent code audits.
Silent Meeting is their latest software app which provides a secure conference calling system. It allows up to 50 participants. Silent Circle says the system means you will no longer have to remember access codes. It has a visual interface which will simplify scheduling, inviting and monitoring conference attendees. Silent Circle Blackphones also come with other preinstalled third-party apps that they have vetted for privacy and security like the Kismet Wireless Wi-Fi Manager which helps you avoid risks from insecure WiFi networks and Remote Wipe.
Silent Circle Services
Our review found that Silent Circle now offers a variety of services that they are gearing more towards enterprise solutions. These services include:
- Silent Store – Silent Store is installed on all Blackphone devices, the world’s first privacy-focused app store features apps from the developer community vetted by Silent Circle
- Silent Manager – Silent Manager gives enterprises a simple and secure web-based solution for managing in place plans, users, groups, and devices
- Silent World – An encrypted calling plan that lets users communicate privately with those who don’t have Silent Phone.
- Subscription plan – Four subscription plans that include both Silent Suite and Silent World (formerly Out-of-Circle Calling) all plans include unlimited receive calls, unlimited member to member, and 120 calling destinations
- Starter – 100 out of circle minutes; $12.95/month
- Intermediate – 250 out of circle minutes; $19.95/month
- Best Value – 500 out of circle minutes; $24.95/month
- Power User – 1000 out of circle minutes; $39.95/month
- Silent World coverage area – countries Silent Circle users can call anyone within privately, with no roaming charges or extra fees.
- North America United States, Canada, Mexico, Guadaloupe
- Caribbean Dominican Republic, Martinique, Puerto Rico, US Virgin Islands, Bermuda
- Central America Costa Rica, Panama
- South America Argentina, Brazil, Chile, Colombia, French, Guiana, Paraguay, Peru, Venezuela
- Africa Morocco, Reunion Island, South Africa
- Europe Andorra, Austria, Bulgaria, Belgium, Croatia, Cyprus, Czech Republic, Denmark, Estonia, France, Gibraltar, Germany, Greece, Hungary, Iceland, Ireland, Italy, Latvia, Lithuania, Luxembourg, Malta, Netherlands, Norway, Poland, Portugal, Romania, San Marino, Slovakia, Slovenia, Spain, Sweden, Switzerland, United Kingdom
- Central Asia Kazakhstan, Uzbekistan
- Eastern Asia China, Hong Kong, Japan, Russia, South Korea, Mongolia, Taiwan
- South-Eastern Asia Brunei, Laos, Malaysia, Singapore, Thailand
- Southern Asia Bangladesh, India
- Western Asia Bahrain, Georgia, Israel, Kuwait, Turkey
- Pacific American Samoa, Australia, Guam, Mariana Islands, New Zealand
- Miscellaneous Voxbone – SA, Voxbone – UN
- Subscription plan – Four subscription plans that include both Silent Suite and Silent World (formerly Out-of-Circle Calling) all plans include unlimited receive calls, unlimited member to member, and 120 calling destinations
Also among the enterprise services they offer is business integration formed by their partnerships with MDM solution providers like Citrix, Soti and Good Technology. This helps pave the way for its increasing roll outs within businesses worldwide.
They also have one of the fasted vulnerability management systems. Critical vulnerabilities in their Silent OS are patched within 72 hours of detection or reporting. They are able to accomplish this because updates come directly from Silent Circle with no carrier delays or waiting periods. Additionally, they have an open source philosophy and to aid in the quick detection of bugs in both their Silent OS software and Blackphone by they sponsoring bug bounty programs for each.
Silent Circle Technology
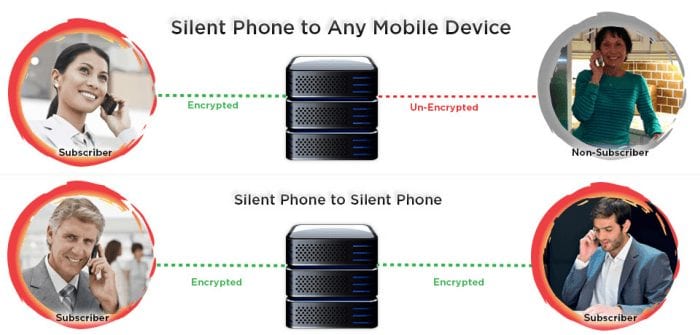
Silent Circle’s Enterprise Privacy Platform is born from a strong set of beliefs in private and secure communications and built on the fundamentally different philosophy of mobile-first architecture. It is designed by some of the best minds in mobile technology, encryption, security and privacy. Security in their network is handled using the Zimmermann Real-time Transport Protocol (ZRTP) designed by Silent Circle co-founder Phil Zimmermann. In accordance with encryption best practices, Silent Circle does not hold or have access to the keys that encrypt your private communications. Accordingly, their communications products use peer-to-peer encryption which means the keys are kept on the sender and recipients machines not the Silent Circle network. Any conversation, video, text, or video teleconference is encrypted from the sender’s device to the other party’s.
A communication using the ZRTP looks something like this:
- The protocol detects when the call starts
- It initiates a cryptographic key agreement between the two callers
- It allows the detection of man-in-the-middle (MiTM) attacks by displaying a short authentication string for the users to verbally compare over the phone
- It then proceeds to encrypt and decrypt the voice and data packets on the fly.
Key negotiations are purely peer-to-peer through the media stream. Keys are unique and are destroyed at the end of each call. The ZRTP protocol also optionally supports Public Key Infrastructure (PKI) if the other VoIP client does not support ZRTP.
Silent Circle Review: Conclusion
Silent Circle is a paid subscription mobile privacy solution that has been designed from the ground up with security and privacy in mind. They provide not only the service, but also the hardware, software, and technology used to implement it which allows them to better meet their users privacy needs. It was originally geared toward individuals who had mobile privacy concerns but has morphed into a global contender to Blackberry in providing a secure mobile enterprise platform for business.
Their hardware includes the original Blackphone, the soon to be released Blackphone 2, with a Blackphone+ tablet to be released in the future. Their original mobile software Silent Suite, consists of Silent Phone, Silent Text, and Silent Contacts. These provide a secure peer-to-peer encrypted solution for VoIP, video, and text. They have developed two new software applications with the enterprise in mind. The first of these, Silent Meetings provides a visual interface for secure video conferencing which simplifies the scheduling, inviting, and monitoring of conference attendees. The second, Silent Manager along with partnerships with major MDM solution providers like Citrix, Soti, and Good Technology provides enterprise managers a secure web-based solution for managing their in-place plans, users, groups, and devices. All of this, plus the introduction of enterprise managed spaces in PrivatOS 1.1, a Silent Store for privacy vetted apps, and the rebranding of their Out-of-Circle Calling service as Silent World makes Silent Circle a serious contender in the mobile enterprise privacy space.
