 Our Perfect Privacy review begins by noting that they started their VPN service in 2008. In 2013, they embarked upon a “reload” of their VPN network infrastructure and resources. As part of this, they have upgraded the majority of their older servers to 1Gb/s bandwidth. Perfect Privacy has also added many new countries and alternate server locations in existing countries. Additionally, they have also added new features and developed in-house custom apps for Windows, Mac OS X and Linux. These apps include features like a top level encryption, a multi-stage kill switch, DNS and IPv6 leak prevention, multi-hop connections, and Stealth VPN. Your personal privacy is further protected by the anonymous payment methods that they accept and a no-log VPN philosophy. As a result Perfect Privacy has grown into a trusted global Internet privacy and security service.
Our Perfect Privacy review begins by noting that they started their VPN service in 2008. In 2013, they embarked upon a “reload” of their VPN network infrastructure and resources. As part of this, they have upgraded the majority of their older servers to 1Gb/s bandwidth. Perfect Privacy has also added many new countries and alternate server locations in existing countries. Additionally, they have also added new features and developed in-house custom apps for Windows, Mac OS X and Linux. These apps include features like a top level encryption, a multi-stage kill switch, DNS and IPv6 leak prevention, multi-hop connections, and Stealth VPN. Your personal privacy is further protected by the anonymous payment methods that they accept and a no-log VPN philosophy. As a result Perfect Privacy has grown into a trusted global Internet privacy and security service.
Pricing and Special Offers
Perfect Privacy offers their VPN service as an integrated package that includes all of its advanced features and support for a variety of devices and platforms. This package is marketed using different term lengths that include: 1 month, 3 months, 6 months, 12 months, and 24 months. Like many VPN providers, they offer discounts on longer term packages.
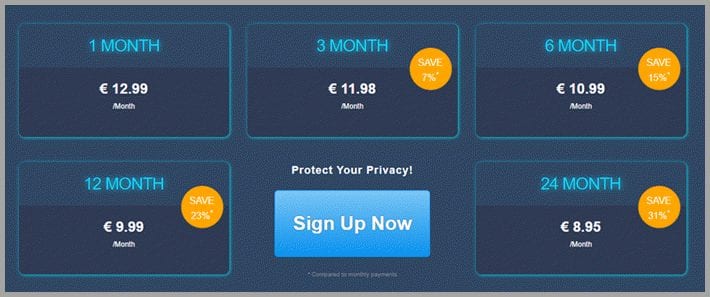
Perfect Privacy is priced as a premium VPN service. They feel that the advanced privacy features that they offer: TrackStop, NeuroRouting, and cascading servers justify this. Thus, their prices starts at € 12.99 or $14.82 for a one month plan. Additionally, you can save 7% on 3 month, 15% on 6 month, and 23% on 12 month plans. However, if you subscribe to a 24 month plan you can get access to their VPN network from just € 8.95 or $10.21 per month. This is a savings of 31% off the single month plan.
Payment Options
Perfect Privacy offers customers many different ways to purchase their VPN service. These include common credit cards like VISA, MasterCard, and American Express, as well as, the Unionpay the global China credit card. Mobile payments can also be made using Mobiamo. They accept PayPal for those who like to conduct their online purchases though a central source. Although they also list Mint, its billpay feature was removed June 30, 2018.

In addition to these, Paymentwall offers many other ways to pay for your VPN service. Perfect Privacy tracks subscriptions using only your randomly created account number and the payment amount. Thus if you want to be more anonymous, you can subscribe to Perfect Privacy using Bitcoin and even cash. Finally, you can pay for your service using bank transfers.
Perfect Privacy Refund Policy
If you are not 100% satisfied with their VPN service after your first purchase, Perfect Privacy will refund your payment. You must request your refund within seven days from the date of initial purchase. This can give you a short amount of time to test the service out and see if it suits our of your VPN needs. Cash or Bitcoin transactions are not eligible for refunds. Perfect Privacy asks that you first give their support team a chance to help you with technical issues before claiming a your refund. We are not sure seven days is enough time for this.
Perfect Privacy VPN Features
Perfect Privacy has many advanced features that only some of the premier VPN services provide. In addition, it combines its own unique combination of these which can be configured from their client software. Others are built into the philosophy employed when they designed their network infrastructure. Some of these features like TrackStop and NeuroRouting are controlled on the server-side and therefore applied to all VPN connections. A list of many of the VPN perks enjoyed by Perfect Privacy uses follows:
- Protocol – support for the most secure OpenVPN an IPSec protocols, as well as, manual support for built-in protocols like IKEv2 and PPTP.
- Encryption – that includes that used by the United States for secure government documents AES-256-CBC, along with lower level choices for traffic which requires less security and greater speed like streaming video.
- No-log philosophy – that is built into their network infrastructure as their service runs on encrypted RAM disks. Thus, nothing is stored when a drive loses power.
- Device support – which includes Windows, macOS, Linux, iOS, Android, and routers.
- TrackStop – which operates on the server-side to use whitelists and filtering to protect users from a variety of different websites. These include ads ab tracking, phishing, social media, fake news, and others.
- Stealth VPN – technology allows you to tunnel all your VPN traffic through either SSH, stunnel or obfsproxy2/3 and vary ports to circumvent firewalls and avoid censorship.
- Cascading VPN servers – allows you to create your own multi-hop paths having up to four levels.
- NeuroRouting – uses AI based on TensorFlow to continuously route your online traffic through the most secure shortest path to the target server of your destination URL.
- VPN Bandwidth – allows unlimited traffic.
- Unlimited simultaneous connections – along with router support protects all devices that connect through the router including TVs, gaming systems and others.
- Only physical servers – are used to form their VPN network with most having 1GB bandwidth and IPv6 addresses.
- Client software – for Windows, Mac OS X, and Linux with advanced privacy features like kill switches, DNS and IPv6 leak protection, proxy support and others.
- Torrent and P2P support – on all servers except those in the United States and France.
- Port forwarding – that includes automatic ports and user configurable ones for applications like torrents.
- Support – via email, forum, FAQ, and remotely through TeamViewer
Perfect Privacy VPN Network and Infrastructure
In 2013, Perfect Privacy began a major upgrade to their VPN network. As a result, most of their network now consists of 1 Gb/s bandwidth metal servers. They do not employ virtual servers in their infrastructure. Additionally, they have also added new locations and extra bandwidth to many their existing ones. Their network also has an internal DNS structure to help guard their uses privacy. These changes have increased the performance and security of the overall Perfect Privacy global network.
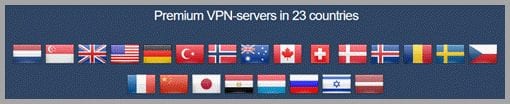
Although relatively small, the current Perfect Privacy VPN service includes over 50 servers in 23 different countries. These are distributed across five continents: Africa, Asia, Europe, North America, and Oceania. Each server has multiple IP addresses which are randomly assigned to all of its users. Most support both IPv4 and IPv6 addresses which future proofs their VPN service by providing full dual stack IPv4 and IPv6 connections. The full list of the Perfect Privacy network servers follows:
- Africa
- Egypt (Cairo)
- Asia
- China (Hongkong), Israel (TelAviv) , Japan (Tokyo), Turkey (Istanbul)
- Singapore (Singapore1; Singapore2)
- Europe
- Czech Republic (Prague), Denmark (Copenhagen), Iceland (Reykjavikm), Latvia (Riga), Norway (Oslo), Romania (Bucharest),
- France (Calais; Paris; Strasbourg),
- Germany (Berlin; Erfurt; Frankfurt1; Frankfurt2; Hamburg; Nuremberg1; Nuremberg2),
- Luxembourg (Steinsel1; Steinsel2),
- Netherlands (Amsterdam1; Amsterdam2; Amsterdam3; Amsterdam4; Amsterdam5; Rotterdam1; Rotterdam2; Rotterdam3; Rotterdam4; Rotterdam5),
- Russia (Moscow1; Moscow2),
- Sweden (Malmoe; Stockholm1; Stockholm2),
- Switzerland (Basel1; Basel2; Zurich1; Zurich2),
- United Kingdom (London1; London2; Nottingham)
- North America
- Canada (Montreal)
- United States (Chicago; Dallas; Los Angeles; Miami; New York)
- Oceania
- Australia (Melbourne)
Every VPN server runs the following services: OpenVPN(UDP), OpenVPN(TCP), IPSec, SSH2, PPTP, Squid Proxy. SOCKS5 Proxy, and TOR. The ports over which these services run are on the membership page of the Perfect Privacy website. Members can also find other information on individual servers there.
Perfect Privacy is also an advocate of P2P and Torrents. However, hosting companies in France and the United States are under strong pressure from media agencies in to curtail filesharing and BitTorrent activity. Often these alleged DMCA violations lead them to terminate their customers contracts. To alleviate this possibility, Perfect Privacy does not allow access to BitTorrent trackers on these servers. All other servers have no such restrictions.
Perfect Privacy User Privacy and Anonymity
As its name signifies Perfect Privacy designed their service with their customers privacy in mind. Although they were originally headquartered in New Zealand, they currently have a split personality. The technical VPN service itself is located in Panama with accounting and data being handled in Switzerland by Vectura. This gives them full control over all infrastructure management tools and internal systems. They feel that this split-structure provides better security for both you and them. Privacy-oriented systems require not only the application of proper technologies but also proper data protections.
Both Panama and Switzerland have federal laws and constitutions that protect your personal information. Neither allow it to be transferred to third parties without notification and/or authorization of the individual involved. Furthermore they also have laws and regulations that protect foreign entities under their jurisdictions from being forced to disclose any such information without following strict legal procedures. Thus, both are ideal destinations for companies operating online privacy services like Perfect Privacy.
Account Information
The fundamental philosophy of the Perfect Privacy service is that they protect their users personal, as well as, online privacy. They do not store any personal payment information. Perfect Privacy monitors customer accounts using only a random assigned account number and the expiration date for the account. Additionally, they state the following in their TOS under the privacy heading.
We try to store as little data as possible, as we can’t be forced to give away something we don’t have in the first place.
Data we need to store:
Your login credentials (username and password)
The email address you provide
The expiration date of your account
As you can see, Perfect Privacy also keeps account credentials: username and assigned password. They use the provided email address to send your credentials. Their website also mentions that a one-time email can be used to register your account. They also state that any and even multiple email addresses can be used to provide on-going support. Additionally, you can choose to encrypt all correspondence by including your public PGP key in the membership area.
Anonymous Payment Methods
Perfect Privacy supports a couple of different levels of anonymous payment methods. These include Bitcoin and cash payments. You can provide pseudo-anonymous Bitcoin payments through Bitpay. Thus, payment wallets must be compatible the Bitcoin Payment Protocol and cannot be sent directly from an exchange. Payment verification can take up to an hour.
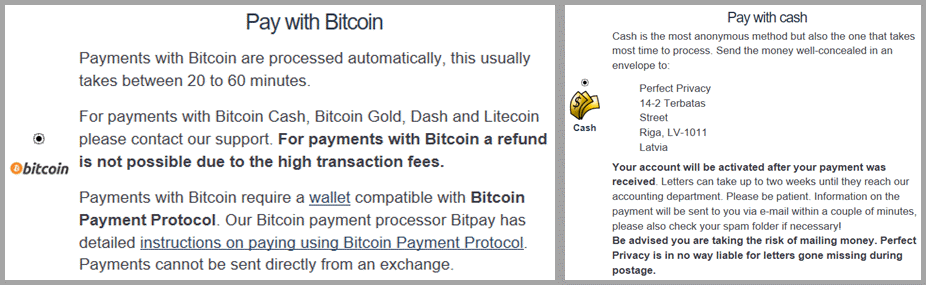
Cash is the most anonymous payment method. However, it can take over two weeks to receive your payment, verify, and activate your account. Additionally, Perfect Privacy is not responsible for lost payments. To pay by cash you need to send the well-concealed money in an envelope to:
Perfect Privacy
14-2 Terbatas Street
Riga. LV-1011
Latvia
Consequently as a good compromise between speed of account activation and anonymity, we feel that payment with Bitcoin is best for those seeking more anonymity.
No Logs and No Latent Data Storage
Perfect Privacy does not log any of their services (VPN, DNS, Proxy SSH, etc) users online traffic. This also includes login and connection data. A continuation of the previous quoted TOS policy further states:
We do not log any logins or connections you make. We solely record the total usage ratio of the servers, i.e. how much traffic is being used on our servers. This data can be publicly viewed on our server status page.
You can see that Perfect Privacy does keep a running total usage ratio of each server. This is used to display a dynamic ” %free” graphic for each sever on their network. This allows their customers to easily see which servers in their region are likely to provide the fastest speeds.
Perfect Privacy takes the no-log idea to its ultimate conclusion. Their servers are hosted on private physical metal servers in premier datacenters around the world. Perfect Privacy does not retain any logs. Furthermore, their infrastructure is built upon this philosophy of no data storage. All of their services run on strongly encrypted RAM (Random Access Memory) disks which have no means of permanent storage.
For those unfamiliar with RAM, any data stored in on it is lost when power is disconnected. You have probably noticed this when you forget to save a document and lost any changes not previously saved if power is interrupted. Similarly, the encrypted RAM disks data can not be copied because it will be destroyed when power is disconnected.
Thus, their will be nothing to copy. This makes it technically impossible for anyone to force them to log your data. Furthermore, they state the following on their website.
Nobody can force us to log your data. If that were the case we would rather discontinue Perfect Privacy than to record your data and compromise your privacy.
Advanced Privacy Features and Common Sense
They have also implemented new proprietary premium VPN features like NeuroRouting, TrackStop, Stealth VPN technology, and cascading VPN servers which can help guard your privacy and overcome online censorship. Their service also provides their users secure DNS, IPv4, IPv6, and WebRTC leak protection, and a firewall based kill switch for users of their custom apps and permanent kill switch installations for mobile devices. We will examine these in more detail later in this Perfect Privacy VPN review.
You can help your own online privacy and anonymity by following common privacy rules. First, clear all browser cookies and use your browser incognito-mode before engaging your VPN. Then, engage the appropriate filters in your ad blocker or TrackStop to limit tracking and malware. Additionally, do not enter you enter your name and address in a public commerce website like Ebay or Amazon.
DNS Leak Test
We tested the Perfect Privacy service on servers in the United States, Europe, and Australia. It exhibited no leaks during our DNS leak testing of connections to individual servers.
So, we wondered how it would do when engaging in a “pressure case” multi-hop connection. We crisscrossed the United States for this test. This is the same setup that we used in our hands on testing of this Perfect Privacy VPN review. First we connected to Chicago and then Dallas. Next we went to Los Angeles and finally New York. We show this multi-hop as follows:
- Chicago »» Dallas »» Los Angeles »» New York
After making our final connection to a server in New York, we conducted an extended DNS leak test to ensure that no leaks occurred.
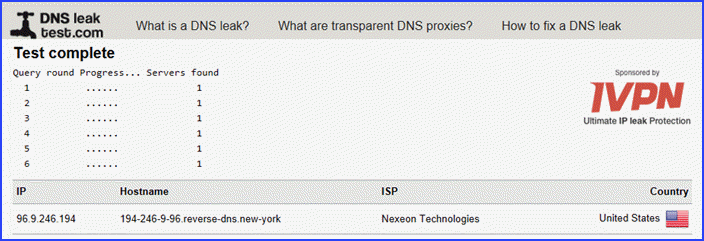 Only one sever was found. This means no DNS leak were observed. We then decided to see what would happen if two of the servers were removed from our server cascade by disconnecting at the third link, Los Angeles.
Only one sever was found. This means no DNS leak were observed. We then decided to see what would happen if two of the servers were removed from our server cascade by disconnecting at the third link, Los Angeles.
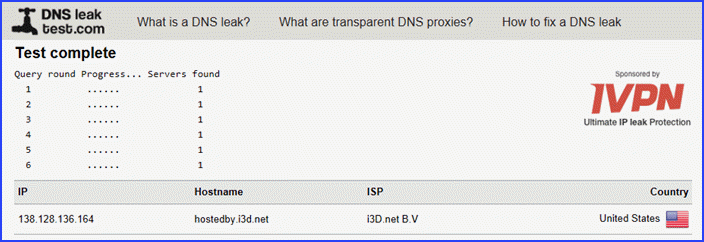 As you can see, only a single server was found. This satisfied us that Perfect Privacy did an excellent job of protecting their users against DNS leaks.
As you can see, only a single server was found. This satisfied us that Perfect Privacy did an excellent job of protecting their users against DNS leaks.
Privacy Summary
In summary, Perfect Privacy has one of the most varied privacy oriented features sets of the all the VPNs that we have reviewed. These include anonymous account creation procedures, advanced VPN privacy features like Neurorouting, a three-stage kill switch, encrypted DNS, and excellent leak protection. Consequently, users of their service can be assured that both their personal privacy, as well as, their online privacy is well protected.
Perfect Privacy Security
All Perfect Privacy services (VPN, proxy, DNS, and other user-accessible services) are hosted on private physical metal servers in premier datacenters around the world. These datacenters follow the latest best practices security procedures for their customers.
Default Custom App Protocols
Perfect Privacy only allows connections by either IPSec or OpenVPN protocols in their VPN manager software. The standardized IETF IPSec protocol provides another encryption alternative. Most modern operating systems support IPSec. Therefore, no extra software is required to use it. Consequently, it can provide higher download speeds with less CPU power. However, you do have to trust the operating system certification authorities (Root-CAs).
OpenVPN is one of the most secure and reliable encryption protocols available today. It also provide a good balance of strong security and fast speed. OpenVPN requires extra software installation. Thus, it uses more CPU power. Perfect Privacy VPN Manager uses hard coded certificates for OpenVPN connections.
Perfect Privacy OpenVPN Implementation
We need to examine the default Perfect Privacy OpenVPN implementation to evaluate the security of their service. Taking a look at a connection log generated by an OpenVPN connection using default settings lets us accomplish this.
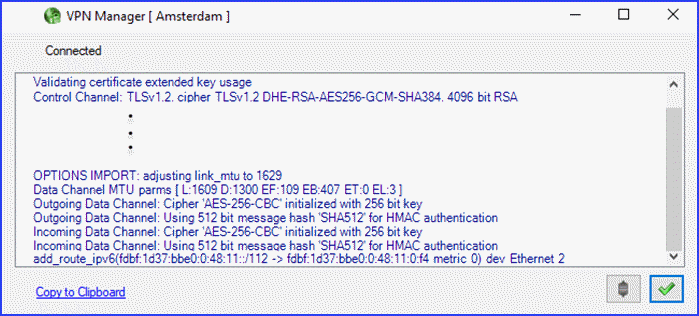 From their connection log file and other sources we find that Perfect Privacy OpenVPN connections uses the following parameter for encryption and data integrity:
From their connection log file and other sources we find that Perfect Privacy OpenVPN connections uses the following parameter for encryption and data integrity:
- Handshake (server/client ) – is by RSA-4096 with 1024 bit Diffie Hellmann keys.
- Data channel cipher – is AES-256-CBC.
- Data authentication – uses HMAC SHA512.
- Control channel cipher – is AES-256-GCM.
- Control channel authentication – uses SHA384 for authentication.
Looking at these, it is easy to see that Perfect Privacy uses high strength encryption algorithms for their VPN service. They use RSA-4096-DHE with SHA-384 for the initial authentication between the server and client. Session keys are renegotiated every 60 minutes to furnish forward secrecy protection. This is similar to the encryption level used by the United States government for “Secret” communications.
Manual Installations
They also have server configuration files to manually install OpenVPN on Android and iOS. These require third party apps: OpenVPN for Android and OpenVPN Connect respectively. Additionally Perfect Privacy recommends IKEv2 with iOS. They have servers configuration files to simply its installation and make it easy to use with their network servers. Perfect Privacy has a guide to use these files to create an On-Demand VPN with iPhone and iPad using IKEv2 in their membership area.
They also have an Android IPSec client which is based on the strongSwan IPSec client. It includes Perfect Privacy configurations, servers, and updates. The client install file (Perfect-Privacy-VPN.apk) can be downloaded from the membership area.
Advanced Security Features
Perfect Privacy also has some premium VPN features like NeuroRouting, TrackStop, Stealth VPN technology, and cascading VPN servers which can increase your online security if you use them. Their VPN manager also provides their users secure DNS, IPv4, IPv6, and WebRTC leak protection, It also includes a three-stage firewall based kill switch. We will examine these in more detail later in this Perfect Privacy VPN review.
Perfect Privacy Security Summary
Perfect Privacy uses OpenVPN as its default primary connection protocol along with AES-256 data encryption. This provides a high level of security for your Internet traffic. Initial handshake uses RSA-4096 with 1024 DH keys to provide authentication. This helps guard against MitM attacks.
They implement forward secrecy session key renegotiation every 60 minutes. Perfect Privacy also has a kill switch to help protect your traffic from unplanned VPN service disconnects. Their app guards against DNS, IPv4/IPv6, and WebRTC leaks. Consequently, we are sure that your Internet traffic is secure when accessing the Perfect Privacy VPN network.
Perfect Privacy Support
Perfect Privacy offers sever different ways of getting general and technical support. They include the following: e-mail (optionally PGP encrypted), contact form, TeamViewer, and forum.
You can send Perfect Privacy an e-mail to support@perfect-privacy.com. If you want to use PGP encryption, you can copy their public key from a link on the “Contact” page on their website. You will also need to toggle the “Send PGP encrypted email only” on in your account membership area.
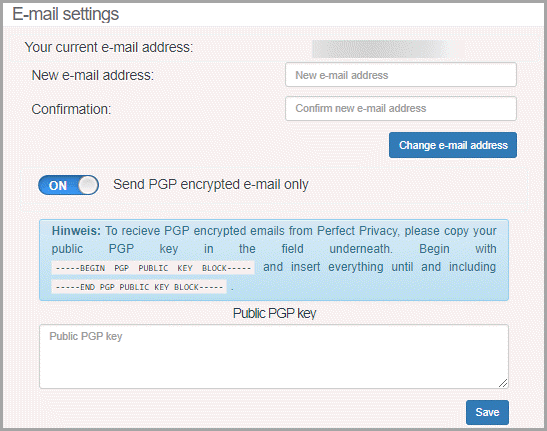 Next, copy your public PGP key into the text box provided. Be sure to include the BEGIN and END Blocks as shown. Users can also get answers to questions from the Perfect Privacy support team through their “Contact form” which is found on their website. You can access this page by clicking on its link “Contact” in the top right-hand side on any page of their website. This area also contains links to their forum, Facebook, Twitter, and login.
Next, copy your public PGP key into the text box provided. Be sure to include the BEGIN and END Blocks as shown. Users can also get answers to questions from the Perfect Privacy support team through their “Contact form” which is found on their website. You can access this page by clicking on its link “Contact” in the top right-hand side on any page of their website. This area also contains links to their forum, Facebook, Twitter, and login.
 This form is very basic and can be used by subscribers, as well as, potential customers. Simply enter a “Name”, “Email address”, “Subject”, and a brief description of your issue in the “Message” textbox. Then, toggle “I’m not a robot” and click “Submit”.
This form is very basic and can be used by subscribers, as well as, potential customers. Simply enter a “Name”, “Email address”, “Subject”, and a brief description of your issue in the “Message” textbox. Then, toggle “I’m not a robot” and click “Submit”.
 We tested the response of the Perfect Privacy support staff by asking about key renegotiation and forward secrecy.
We tested the response of the Perfect Privacy support staff by asking about key renegotiation and forward secrecy.
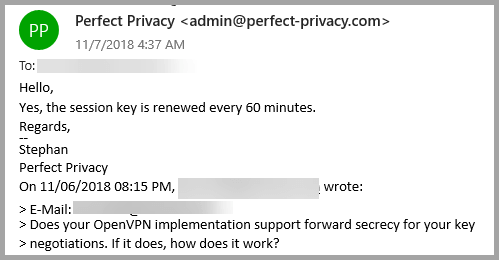 We received a response in about 9 hours. What is more, the response addressed our question in a well-worded succinct answer. Therefore, we were satisfied with their support. It you would like for one of their support personnel to remote into your machine, you can send an email or ticket to be informed about the next time slots available for help via TeamViewer. You can also create a forum account and ask questions there or browse their FAQ database. Finally, you can get security news from their blog, Facebook, or Twitter.
We received a response in about 9 hours. What is more, the response addressed our question in a well-worded succinct answer. Therefore, we were satisfied with their support. It you would like for one of their support personnel to remote into your machine, you can send an email or ticket to be informed about the next time slots available for help via TeamViewer. You can also create a forum account and ask questions there or browse their FAQ database. Finally, you can get security news from their blog, Facebook, or Twitter.
Perfect Privacy VPN: Hands-On
Perfect Privacy has client software, Perfect Privacy VPN Manager which will run on the following platforms:
- Windows 7, 8, 10, Vista
- macOS 10.9 and later
- Ubuntu, Linux Mint, and other Debian flavors
Additionally, they also have a strongSwan based IPSec Android app that you can download from the download page of their membership area. Finally, you can connect to their network using their Perfect Privacy SSH client.
In addition to their clients, you can connect to their network with OpenVPN using various third party clients and downloading their appropriate configuration files. They also support manual installation of IKEv2 using IPSec pre-shared keys and even PPTP. Although, you should not use PPTP unless nothing else works because it is now considered unsecure.
Creating a Perfect Privacy VPN Account
Once you select the Perfect Privacy VPN term plan the account creation process will initiate for first time purchasers. In this case, a 24-month plan has been chosen because it provides the best deal for their service. You will have seven days to see if their service is right for you so you should choose the plan you are most comfortable with.
 Once you have made your service duration, click “continue »”. This will scroll to the “Username” section for new customers or existing account holders. If you are a new user, enter a ‘Username”, “E-mail address” and then select “continue »”. It you are an existing account holder, toggle “Account extension” and enter your “Username”. Your new account details will be sent to your existing email on file and the email field below will be disabled.
Once you have made your service duration, click “continue »”. This will scroll to the “Username” section for new customers or existing account holders. If you are a new user, enter a ‘Username”, “E-mail address” and then select “continue »”. It you are an existing account holder, toggle “Account extension” and enter your “Username”. Your new account details will be sent to your existing email on file and the email field below will be disabled.
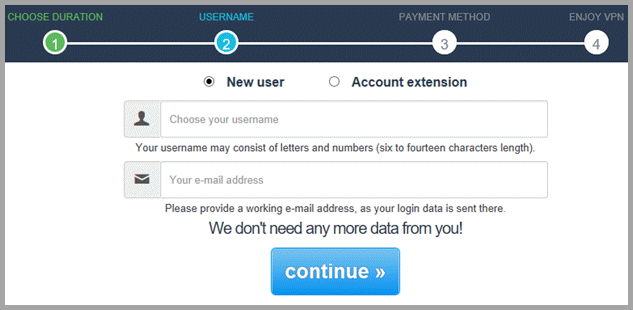 Regardless of whether you are a new or existing account holder, after you click on the “continue »” button you will move on to select your chosen payment method. Select your payment method and complete your purchase.
Regardless of whether you are a new or existing account holder, after you click on the “continue »” button you will move on to select your chosen payment method. Select your payment method and complete your purchase.
 The support team at Perfect Privacy will send you a welcoming email. This email will also contain your account certification credentials “Username” and “Password”. These credentials will also allow you into your Perfect Privacy membership page of their website.
The support team at Perfect Privacy will send you a welcoming email. This email will also contain your account certification credentials “Username” and “Password”. These credentials will also allow you into your Perfect Privacy membership page of their website.
Hands On: Perfect Privacy VPN Windows Client
You can obtain the appropriate client software for your device from the “Download” page of the membership area. This page also contains the configuration files that you need to run the Perfect Privacy service with other third-party clients. First select the icon that represents the platform your device runs on. Your choices include: Windows, macOS, iOS, Android, and routers.
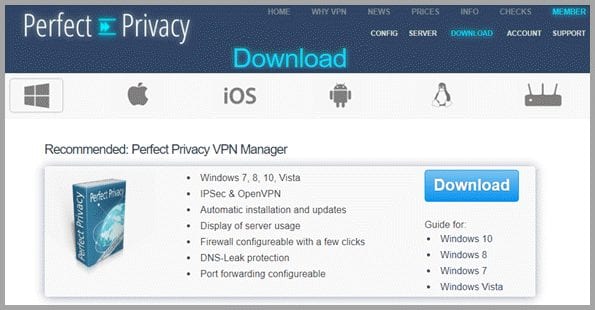 In this case, we chose the Windows platform. Perfect Privacy recommends that Windows users install their VPN Manager to take advantage of its advanced privacy features. Their manager will made it easy to connect to their network and you can configure their more advanced features with just a few clicks. Click on the “Download” button to copy the installation file to your computer.
In this case, we chose the Windows platform. Perfect Privacy recommends that Windows users install their VPN Manager to take advantage of its advanced privacy features. Their manager will made it easy to connect to their network and you can configure their more advanced features with just a few clicks. Click on the “Download” button to copy the installation file to your computer.
Installing the Perfect Privacy VPN Windows Client
After the installation file for the Perfect Privacy VPN has been copied to your Windows device, run it as administrator and allow it the permissions it needs to make changes to your computer. When the setup file opens, select the “Install” button.
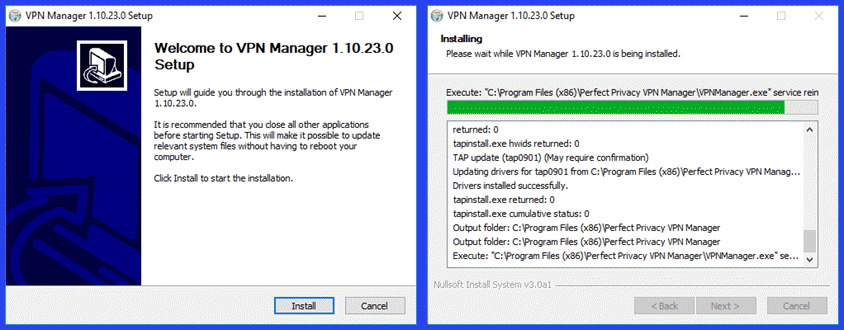 This will begin the extraction and installation of the files needed to support the Perfect Privacy VPN Manager. This may include updating the TAP driver which may require user confirmation.
This will begin the extraction and installation of the files needed to support the Perfect Privacy VPN Manager. This may include updating the TAP driver which may require user confirmation.
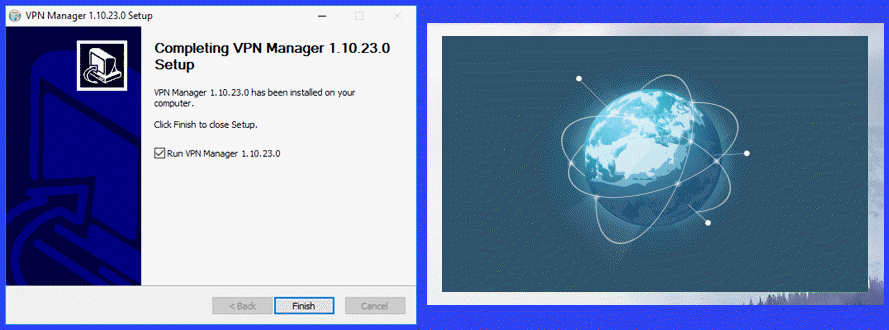 After a few minutes, the Perfect Privacy VPN Manager setup completes. The toggle to auto run the Windows client is set. If you want the client to startup once installation finishes, just click on the “Finish” button. Else, toggle it off and select “Finish”. You can start the client later from its desktop shortcut. When you first open the VPN manager, it displays a temporary startup screen.
After a few minutes, the Perfect Privacy VPN Manager setup completes. The toggle to auto run the Windows client is set. If you want the client to startup once installation finishes, just click on the “Finish” button. Else, toggle it off and select “Finish”. You can start the client later from its desktop shortcut. When you first open the VPN manager, it displays a temporary startup screen.
Perfect Privacy VPN Manger Settings
After a couple of minutes, the settings menu opens. This screen contains the following tabs: Perfect Privacy Settings, Program Settings, Firewall and DNS, IP and Ports, Cascading and Stealth, and Other. Changes made to the tabs on this page are saved when you “Close” the settings page.
Settings: Perfect Privacy Settings
When the Perfect Privacy VPN Manger first opens, the “Perfect Privacy Settings” tab is displayed. This is where you enter the login credentials (“Username” and “Password”) that their support team emailed you earlier. Your credentials will be saved once you login and close the settings page. You can also choose between the IPSec and OpenVPN protocols from this screen.
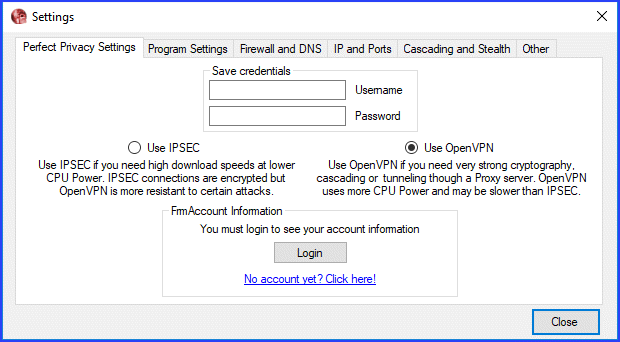 IPSec is less CPU intensive may be faster on slower devices. It also does not support server cascading or stealth. Most users will probably use OpenVPN to take advantage of its selectable strong cryptography and other advanced features. After you login your account expiration date will also be displayed here.
IPSec is less CPU intensive may be faster on slower devices. It also does not support server cascading or stealth. Most users will probably use OpenVPN to take advantage of its selectable strong cryptography and other advanced features. After you login your account expiration date will also be displayed here.
Settings: Program Settings
The Program Settings are divided into three categories: Startup, Severlist, and OpenVPN settings. The startup settings will allow you to start the client when Windows boots up. It will also let you run it minimized and select a server to auto-connect to.
You can choose how you want the servers on the main connection dashboard to be sorted. The options include: Name, Ping, Traffic, and Country. You can also toggle to show the high bandwidth servers first. Finally, you can invert the bandwidth panel to show “Current traffic” instead of the default “Available bandwidth” graphics.
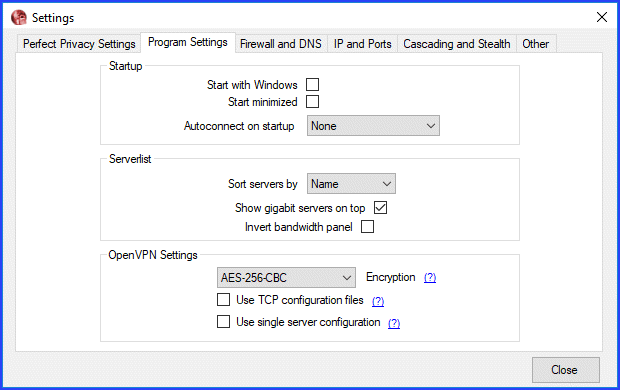
The last category is OpenVPN Settings. You can change your encryption cipher from here. It will let you vary both the algorithm and strength. Choices include the following:
- Strong encryption – should be used if the security of your online traffic is your main consideration.
- AES-256-GCM – can be faster on some hardware.
- AES-256-CBC – is the default for most users who want strong encryption.
- Camellia-256-CBC – is European Union standard and substitute for US government AES standard.
- Weak encryption – can sometimes provide better performance for situations where enhanced security is not your primary goal or if you are running service on a weak CPU device.
- AES-128-GCM – can be faster on some hardware.
- AES-128-CBC – is the default for most users who do not need strong encryption.
- Camellia-128-CBC – is an alternate encryption standard.
If Stealth VPN is not activated, you can also choose to switch between UDP and TCP. UDP is the default and usually provides better speeds. Therefore, unless you have an unstable connection you should use it. The last toggle:
- Use single server configuration – shows all servers at a location with individual bandwidth and usage for each server instead of a composite on the main connection screen.
 Settings: Firewall and DNS
Settings: Firewall and DNS
Under Firewall and DNS you can configure the level of your integrated firewall (kill switch) and DNS leak protection. You can change the settings for the firewall and DNS leak protection independently. However, they recommended to use the same settings for both. Both can be set to three levels:
- Activate while tunnel is active – engages the kill switch and DNS protection only when you are connected to a Perfect Privacy server. If your VPN connection accidentally drops, then, your Internet service will be blocked till it is restored. If you disconnect normally the kill switch will not engage.
- Activate while program is active – keeps the firewall and DNS protection as long as the Perfect Privacy client is running, regardless of its connection state. This means if you start the client, your internet connection will be blocked until you connect to Perfect Privacy. If you quit the client, normal Internet operation will be restored.
- Activate permanently – means that Internet traffic will only be allowed through the Perfect Privacy VPN network.
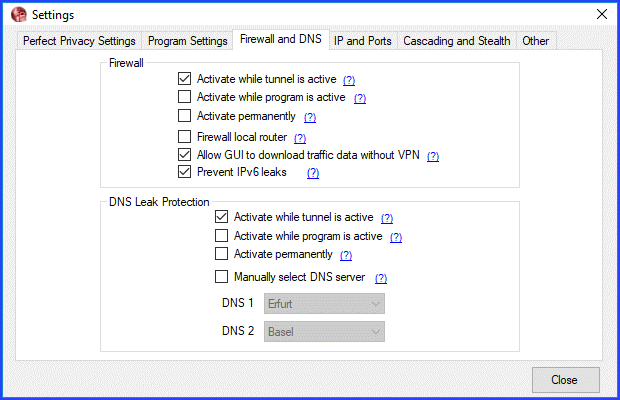
The other Firewall settings:
- Firewall local router – when toggled, will prevent direct access to your router (LAN will still work but you cannot send any packets directly to the router).
- Allow GUI to download traffic data without VPN – will allow the client to check for Perfect Privacy updates and display the server load in the main window even if firewall protection is activated.
- Prevent IPv6 leaks – should be activated to prevent IP leaks over IPv6. This is necessary if your ISP provides IPv6 connectivity.
By default, DNS servers are randomly assigned . However, you can toggle:
- Manually select DNS server – to choose permanent Perfect Privacy nameservers. Simply select your choices from the list boxes for DNS 1 and DNS 2.
When the firewall and DNS leak protection is activated, it will be displayed in the upper right as “F” and “D”, respectively.
Settings: IP and Ports
In this section you can choose whether you want to get a randomly assigned IP address from the server. This is the default recommended for most users for better privacy.
You can also set up port forwarding. There are two types of port forwarding that you can enable:
- Default – will create three default port forwarding. The ports for the default forwarding are always 1XXXX for the first forwarding, 2XXXX for the second and 3XXXX for the third. The XXXX is determined by the last 12 bits of the internal IP address. We will see an example of this later in our Perfect Privacy review.
- Custom – lets you enter a port forwarding manually. Custom port forwarding applys only to your chosen server. Therefore, first choose a server in the selection field below and click on “Set”. This will enable the fields below it. You will then be able to add either/or:
- A 1 to 1 port forwarding – will add a random port forwarding.
- A forwarding to a port of your choice – will use a random server-side port.
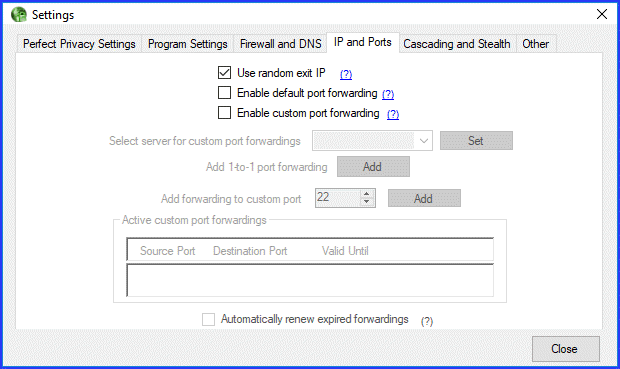
The custom ports forwarded will be displayed in “Active custom port forwardings”. These will expire after seven days unless you toggle, “Automatically renew expired forwardings”
Settings: Cascading and Stealth
This settings tab is divided into three categories: Cascading, Stealth VPN, and Proxy Settings. If you toggle “Enable cascading” on, you can chose from 2 to 4 for the maximum number of hops. We will see how the client handles this later in our Perfect Privacy review.
If you live in a country that censors the Internet like China, Saudi Arabia, or Iran, then you may want to “Enable Stealth VPN” to bypass government restrictions. You can tunnel all your VPN traffic through either SSH, Stunnel or obfsproxy3. Alternately, you can also switch between ports 22 (SSH), 53 (DNS), 443 (SSL) or a random high port. It can also help you circumvent firewall filters on restrictive networks (Schools, Universities, Companies, etc), since traffic on port 443 and 53 is often allowed. Stealth VPN uses TCP and disables proxy support.
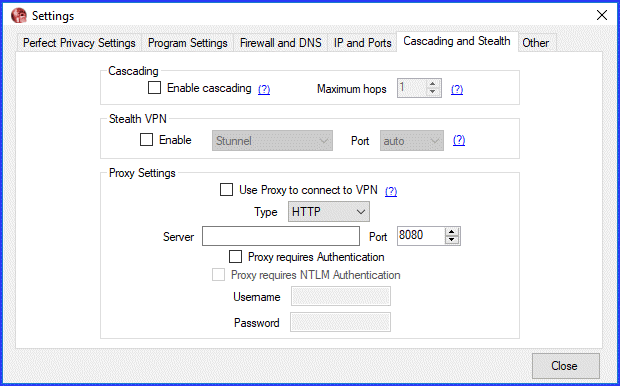
Finally if you want to use a proxy server to connect to the Perfect Privacy, you can set it up here. You can chose between HTTP and SOCKS protocols. Enter the server IP or name and select the proper port number. Be sure to enable the proper authentication if needed and your “Username” and “Password”.
Settings: Other
The last tab of the settings will let you change the debug level and view the debug log. This can be useful for troubleshooting connections. You can also look at the log from here and copy it if you need to. Although updates are performed periodically, and automatically when you open the other tab, you can also manually check for the latest one. You should only use the reset button if told to by a Perfect Privacy technical support representative as it will reset the TAP-Adapters as well as the firewall and DNS leak protection or you need to reinstall TAP and IPSec adapters.
 Before we look at the Perfect Privacy VPN Manager for Windows in action, let us first look at some of the server-side settings.
Before we look at the Perfect Privacy VPN Manager for Windows in action, let us first look at some of the server-side settings.
Perfect Privacy Server-Side Configuration
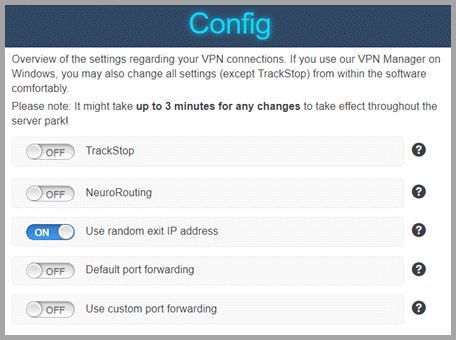
You can configure some settings regarding Perfect Privacy VPN connections on the server. These include the following:
- TrackStop – allows you to block unwanted domains directly at the VPN level.
- NeuroRouting – increases the security and anonymity of Perfect Privacy VPN connections through the application of artificial intelligence.
- Use random exit IP address – increases security, privacy, and anonymity by making traffic analysis more difficult.
- Default port forwarding – provides you three port forwardings to your corresponding local ports upon establishment of a Perfect Privacy VPN connection. These ports depend on your internal VPN IP address.
- Custom port forwarding – provides you up to five custom port forwardings. These are limited to one server group (location) at a time. If you switch locations, all current port forwardings are deleted.
TrackStop and NeuroRouting are applied to any device you use to access their VPN network. The random exit and port forwarding settings can be controlled from within the Perfect Privacy VPN Manager Client settings, as well as, from the membership config area. If set on the server-side, it will take a few minutes for them to propagate through the network. You will also need to restart the client for them to be applied to it if you make changes while it is running. You can see how these work above in our Settings: IP and Ports section.
 TrackStop
TrackStop
TrackStop is an advanced security privacy feature provided by the Perfect Privacy service. It works by using their nameservers to block pre-defined blacklists to filter out specific domains. You can control the types of domains that are blocked by activating one or more of the given filters. Child protection, tracking and advertisement, fraud filters, and possibly fake news will help increase user security and privacy. The others are of limited utility in our opinion but feel free to play with them if you want.
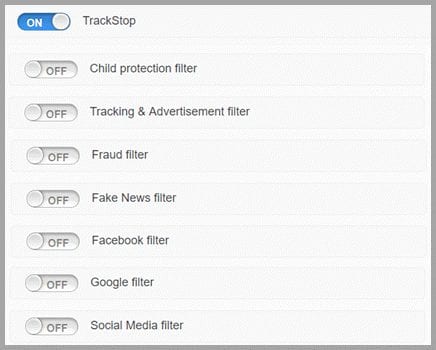 The filters that you can choose to activate include the following:
The filters that you can choose to activate include the following:
- Child protection – This filter will block a lot of websites that are inappropriate for children. This includes pornographic content but also gambling websites. Additionally this filter contains the block lists for tracking & advertisement as well as fraud. Thus these individual filters do not need to be activated if this filter is activated.
- Tracking and Ads – Activate this filter and protect yourself by blocking over 30.000 tracking and advertisement domains. We recommend for security and privacy reasons.
- Fraud – Activate this filter to block over 45.000 known malware domains and about 20.000 phishing domains. We recommend for security reasons.
- Fake news – Block list with known fake news domains using a publicly available filter list hosted on GitHub to which anyone can contribute.
- Facebook – Facebook is notorious for tracking users and collecting as much data as possible from them. This not only affects Facebook users but anyone who is visiting websites that show a Like-Button or other content from Facebook. For anonymity reasons, you can activate this filter and block all Facebook domains.
- Google – Warning: This blocks all Google domains, including Youtube, ReCaptcha and other services from Google used on many websites! This is not very practical but if you want to find our how much the Internet relies on Google, you can temporarily set this filter.
- Social Media – Most users will not select this filter either. However if you are the do not want to access social media while using the VPN network, you could set this filter. It will block Facebook, Twitter, Tumblr, Instagram, Google+, Pinterest, MySpace and LinkedIn among others.
NeuroRouting
NeuroRouting is based on Google’s open-source library for machine learning (TensorFlow). It works by analyzing the routes to the target website and then determines how to minimize traffic outside their encrypted VPN network. In practice, this means that the Perfect Privacy VPN server nearest to the destination is always used. The shortest route to minimize traffic exposure is then determined.
This provides a more secure path for your Internet traffic. Your data is sent encrypted from one VPN server to the next. It continues to do this till it reaches the server closest to the server hosting your destination URL. Ideally, the target server is located in the same data center, in which case the traffic does not appear on the Internet at all. Else, it still has limited exposure on the Internet.
These routes are constantly being dynamically recalculated and change as target destination URL changes. Additionally the external VPN IP changes depending on the destination. This makes it hard to predict which routes your traffic is using which increases your online privacy.
For example, suppose a user is accessing websites hosted in Australia, the United States, Brazil, and Russia. Each website takes a different, encrypted, multi-hop route through the Perfect Privacy VPN network. The user will broadcast a different IP address for each website at the same time, corresponding to the last server in the chain. You can easily test this by accessing different Check-IP websites. Depending on where the web server is located, a different VPN IP address will be displayed.
You can turn the NeuroRouting feature on or off on the config page of the membership area of their website with just a single click. Note, it may take a few minutes to update. It works on all available protocols (OpenVPN and IPSec) and all supported devices. You should not use this feature if you want to use a particular VPN server connection. Neither should NeuroRouting be used for downloading larger files (e.g. torrents) to ensure that you always use a fast Gigabit server.
Using the Perfect Privacy VPN Manager for Windows
Now that we have looked at the settings of the Perfect Privacy VPN Manager, let us examine its main connection dashboard. The dashboard is pretty basic. It contains file column headings: Country, Server, Ping (ms), and Available bandwidth.You can click on a column heading to sort it. Default sort is by alphabetical server. The last column has no heading. It just displays the connect (plug) and show log (magnifying glass) icons.
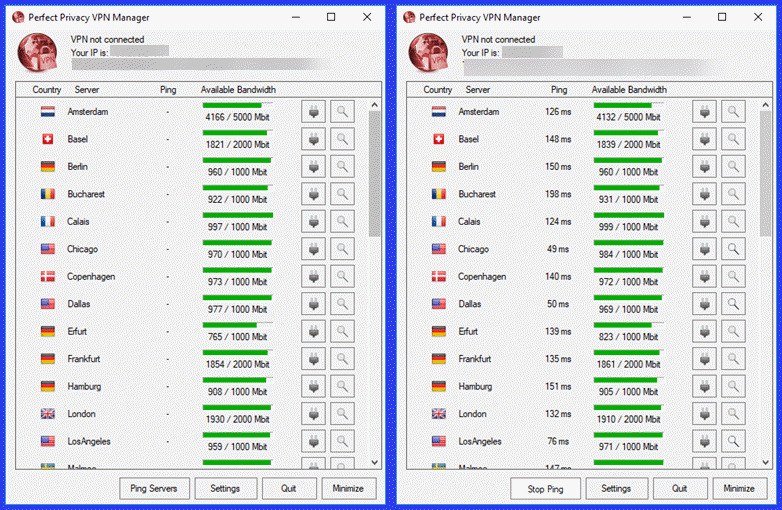 The top of the dashboard displays an icon representing the current connection state. A red indicates no connection, yellow shows a connecting state, and green means that you have successfully connected to the Perfect Privacy network. Your current external IP address and DNS server is also shown.
The top of the dashboard displays an icon representing the current connection state. A red indicates no connection, yellow shows a connecting state, and green means that you have successfully connected to the Perfect Privacy network. Your current external IP address and DNS server is also shown.
You can also ping the VPN servers which will display the real-time ping times (ms), Open the Settings menu, and quit or minimize the client by clicking on the appropriate button. To connect to a server, just click on the plug over from the server name.
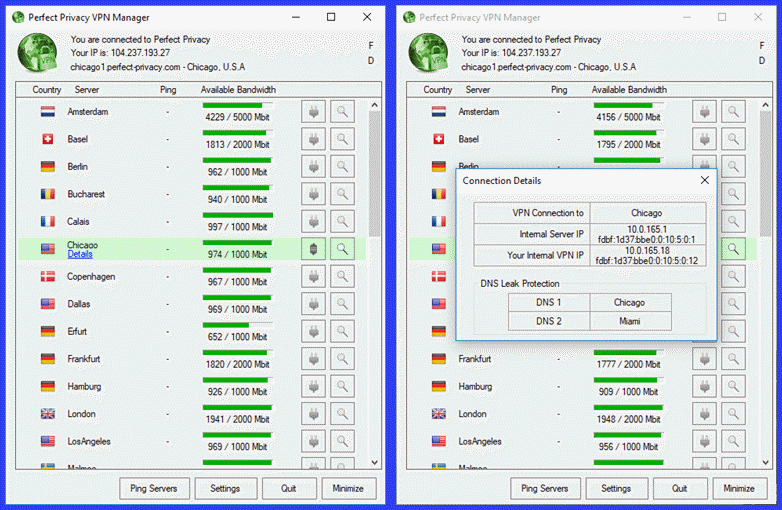 Once the connection successfully completes (green icon), the row containing the VPN that your are connected to is highlighted in green. You can then click on the blue “Details” link to see more information about the connection. Notice your IP address has changed and you have been randomly assigned DNS 1: Chicago and DNS 2: Miami.
Once the connection successfully completes (green icon), the row containing the VPN that your are connected to is highlighted in green. You can then click on the blue “Details” link to see more information about the connection. Notice your IP address has changed and you have been randomly assigned DNS 1: Chicago and DNS 2: Miami.
Also notice the F and D in the upper right of the dashboard. This indicates that the firewall (kill switch) and DNS protection have been enabled for the current connection. To disconnect, simply tap the plug again. You will also see notices regarding Firewall and DNS changes when connecting and disconnecting from the VPN server.
 Now that we have seen how easy it is to connect and disconnect from the Perfect Privacy network, let us examine some of its more advanced features.
Now that we have seen how easy it is to connect and disconnect from the Perfect Privacy network, let us examine some of its more advanced features.
Level 4 Cascaded Server Connection
This example assumes that we have enabled server cascading with four hops. You can see that the connections are numbered from 1 to 4. This shows the order that the servers were cascaded through.
- Chicago »» Dallas »» Los Angeles »» New York
Once server level 4 cascading is enabled, the server plugs are not disabled until the chosen number of cascaded servers are connected (which is four in our case).
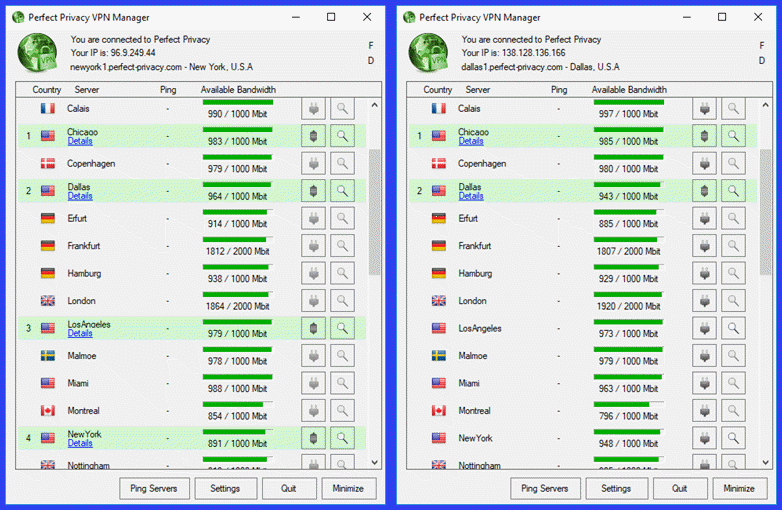 Notice in the second image we have disconnected the Los Angeles server. This removes the New York server as well. Also notice, the other server plugs are no longer disabled. We could create a new level 4 cascaded connection by choosing two new servers. These are the same setups that we used in our pressure DNS leak test previously in this review.
Notice in the second image we have disconnected the Los Angeles server. This removes the New York server as well. Also notice, the other server plugs are no longer disabled. We could create a new level 4 cascaded connection by choosing two new servers. These are the same setups that we used in our pressure DNS leak test previously in this review.
Perfect Privacy IP and Port Usage Example
In this example, we have chosen to use a random exit IP address with both default and custom port forwarding. The Chicago location has custom ports attached to it . We also created both a 1 to 1 port and added a custom port forwarded to local port 22. Source ports on the server-side are chosen at random. In the case of the 1 to 1 port the destination port is the same as the source port. However in the second case, a custom random source port is then forwarded to the local destination port 22.
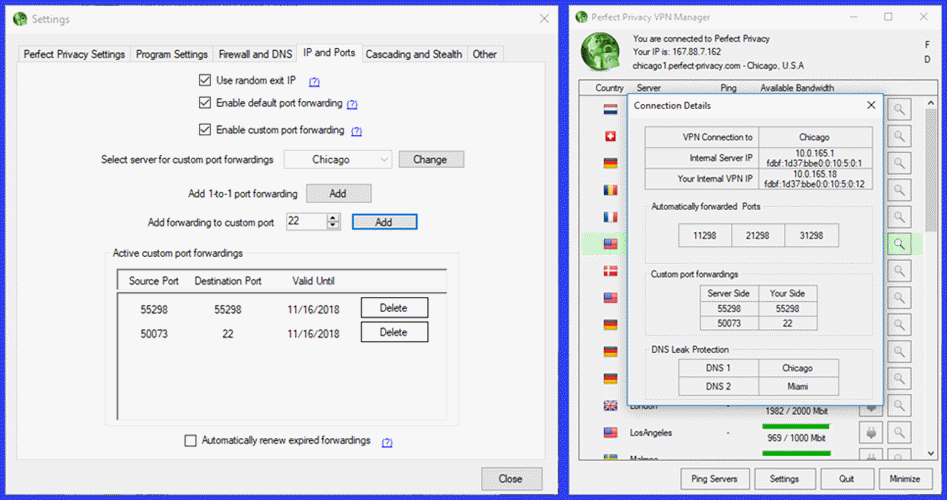 A bracketed PF will now be shown beside the Chicago server which indicates that it has custom forwarded ports. After connecting to the Chicago location and examining its connection details forwarded ports can be seen along with the internal IP addresses and DNS servers.
A bracketed PF will now be shown beside the Chicago server which indicates that it has custom forwarded ports. After connecting to the Chicago location and examining its connection details forwarded ports can be seen along with the internal IP addresses and DNS servers.
In addition these, three automatically forwarded ports are shown. These are determined as follows:
Example: In this example the internal VPN IP is 10.0.165.18. Converting to binary this is 00001010 00000000 101000101 00010010. Converting the last 12 bit 010100010010 to decimal results in 1024+256+16+2 = 1298. So the forwarded ports will be 11298, 21298, and 31298.
This is the same as the automatically forwarded ports shown in the above image.
Perfect Privacy VPN Manager for Windows Summary
The client software is easy to download and install. It is also simple to use. Connections can be made by just clicking on the plug icon for the location you want to connect to. Disconnect by clicking on the plug a second time. If cascading is not enabled, you must disconnect from your current VPN server to choose another. The client also supports extra privacy features that are easy to configure and use, both on the server and the client side.
Hands-On: IPSec Android App
Installing the Android IPSec/IKEv2 App
First, set your device to download files from a source other than the Google Play store in its security settings. Next, open the Perfect Privacy website on your Android phone and then login to your account. Once there, open the “Download” page of the membership area and select the Android platform. Scroll to the Perfect Privacy Android IPSec client .apk file and tap on it.
Instead of downloading it, tap on the blue “Perfect Privacy-VPN.apk” link. This will open an install screen for the client. Tap on “Install” and wait for it to finish.
 After the app is installed, tap “Open” to run it. This will display the app connection dashboard. Before we use it to connect, let us login to the software. Tap on the menu icon (three horizontal dots) at the top of the dashboard and select “Set login credentials. Enter the Username and Password that you received in your welcoming email from the Perfect Privacy team.
After the app is installed, tap “Open” to run it. This will display the app connection dashboard. Before we use it to connect, let us login to the software. Tap on the menu icon (three horizontal dots) at the top of the dashboard and select “Set login credentials. Enter the Username and Password that you received in your welcoming email from the Perfect Privacy team.
 Tap on “Save” to save them and return to the main connection screen. Once there tap on the Chicago location to connect to it. You will need to accept the VPN setup request by tapping on “OK”. Your will see a “Connecting” status for your chosen profile Chicago.
Tap on “Save” to save them and return to the main connection screen. Once there tap on the Chicago location to connect to it. You will need to accept the VPN setup request by tapping on “OK”. Your will see a “Connecting” status for your chosen profile Chicago.
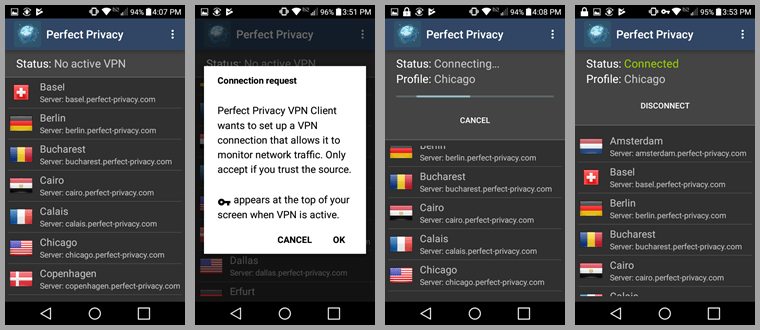 Shortly, this will be followed screen followed by a green “Connected” status for the Chicago location. From here you can select “Disconnect” to leave the Chicago server or you can select another location like Dallas. This will open a small info sub screen. Tap on “Connect”. The status now show first “Connecting” and then green “Connected” to the Dallas VPN server.
Shortly, this will be followed screen followed by a green “Connected” status for the Chicago location. From here you can select “Disconnect” to leave the Chicago server or you can select another location like Dallas. This will open a small info sub screen. Tap on “Connect”. The status now show first “Connecting” and then green “Connected” to the Dallas VPN server.
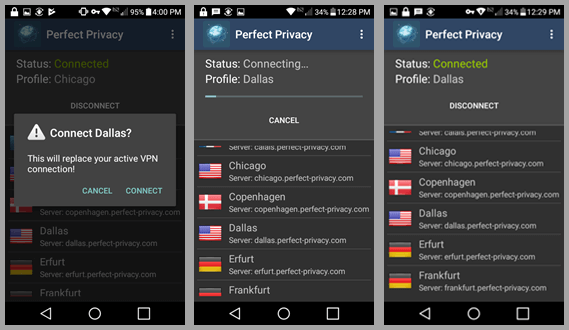 Now, tap on “Disconnect”. The status will now show “Disconnecting” Dallas. The “No active VPN” message follows . Swipe down and then tap on the Amsterdam server to connect to it.
Now, tap on “Disconnect”. The status will now show “Disconnecting” Dallas. The “No active VPN” message follows . Swipe down and then tap on the Amsterdam server to connect to it.
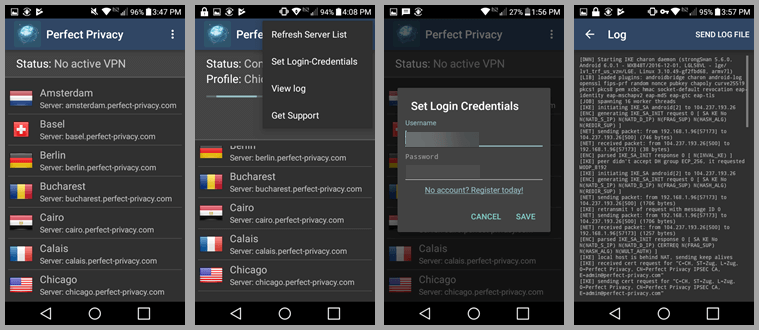
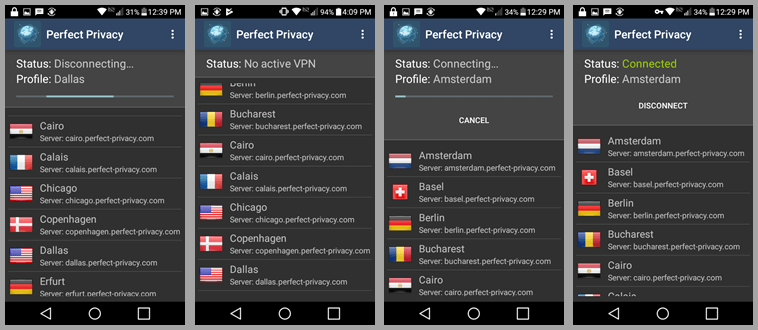 This will again display the familiar status “Connecting” and then the green “Connected” to a VPN server in Amsterdam. Now disconnect from the Amsterdam server. Once the status displays “No active VPN”, open the menu. The menu consists of four items:
This will again display the familiar status “Connecting” and then the green “Connected” to a VPN server in Amsterdam. Now disconnect from the Amsterdam server. Once the status displays “No active VPN”, open the menu. The menu consists of four items:
- Refresh server list – which displays a screen message while refreshing the Perfect Privacy VPN server list. This happens very quickly.
- Set login credentials – we used earlier when we logged. Notice, the client saved our credentials so we do not have to enter them the next time it is opened.
- View log – displays the connection log for the client and lets you save it to a file.
- Get support – is just a link to the contact area of the Perfect Privacy website.
 Summary of the Perfect Privacy IPSec Client
Summary of the Perfect Privacy IPSec Client
The client is easy to install once you know the secrets but it took a while on our Android phone before we discovered them. Once it is installed, you can connect to a VPN server with just a single tap. Changing server locations can be done by simply choosing another location and connecting to it in a couple of screen taps. Else you can connect by first disconnecting from your current VPN server and then choosing another.
Perfect Privacy VPN Speed Test
We tested the Perfect Privacy service with their VPN manager for Windows software. The test uses the OpenVPN (UDP) protocol with AES-256-CBC encryption. The service performed good on our speed tests. We were pleased with its overall performance. Their is some loss of speed is due to the encryption overhead that their encryption algorithm incurs.
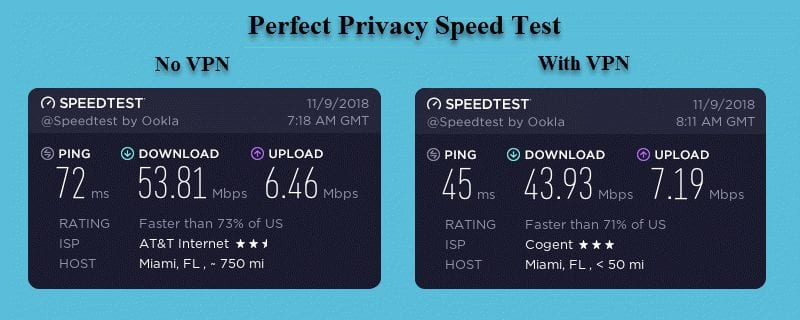 You can see that our download speed was 53.81 Mbps without the VPN connection but decreased to 43.93 Mbps when using the Perfect Privacy VPN network. This is a drop of about 18.3% to a server in Miami, FL. We found similar results when using other locations. There was a 20.1% loss to a server in Chicago, IL and 32.6% to a server in Melbourne, AU. As expected, we experienced greater speed loss as the distance and ping times are increased.
You can see that our download speed was 53.81 Mbps without the VPN connection but decreased to 43.93 Mbps when using the Perfect Privacy VPN network. This is a drop of about 18.3% to a server in Miami, FL. We found similar results when using other locations. There was a 20.1% loss to a server in Chicago, IL and 32.6% to a server in Melbourne, AU. As expected, we experienced greater speed loss as the distance and ping times are increased.
Even with this loss in speed, the 40+ Mbps speeds is still fast enough for most VPN applications. Even the 26+ Mbps of the Melbourne connection is sufficient for streaming media. This speed reduction is worth the extra online security and privacy that you gain from using the Perfect Privacy service. You could experience different results in your region of the world depending on your ISP.
Perfect Privacy VPN Review : Conclusion
Perfect Privacy has been in the VPN business since 2008. They are dual headquartered. Accounting and data management is handled in Switzerland, while their technical implementation is in Panama. Both are good locations for online security businesses. They both protect personal privacy in their laws, as well as, their constitutions.
Perfect Privacy requires only a “Username” and valid “email address” to create your account. They then assign you an ” Account password” and then email you your credentials. Additionally, you can make anonymous payments to help protect your privacy and anonymity. Perfect Privacy does not store Payment info with your account. Perfect Privacy monitors user accounts with a random number associated with the account and the termination date. This means the only information that they keep for a customer is username, password, email address, and termination date. What is more you can use a new email address each time you contact them is you want to.
Perfect Privacy designed their network infrastructure with the online privacy of their customers in mind. They do not log any individual connection or VPN activity. This includes IP addresses, connection times, DNS requests, sites visited, and etc. The only VPN information that they keep is a running total of the “% free” space of their servers. The only information that they store is the total usage ratio of the servers, which they display on their public server status page. Additionally, Perfect Privacy built their infrastructure upon this philosophy of no data storage. All of their services run on strongly encrypted RAM (Random Access Memory) disks. The data is destroyed if the disk loses power.
Perfect Privacy initiated an upgrade of their VPN service at the end of 2013. Since that time, they have increased both the coverage and performance of their network architecture. They have added more locations and increased the number of servers at existing locations. Additionally, they have increased the bandwidth of most of their VPN servers to 1Gbps and added support for IPv6 addresses. They only use unshared, physical servers in their VPN network.
They currently have a small to mid-sized network with over 50 servers in 23 countries different countries. All of their VPN servers runs the following services: OpenVPN(UDP), OpenVPN(TCP), IPSec, SSH2, PPTP, Squid Proxy. SOCKS5 Proxy, and TOR. They have guides for installing these service on a myriad of devices. Perfect Privacy has servers in Africa, Asia, Europe, North America, and Oceania. Each VPN server assigns Random IP addresses to each customer from a list available to it. Their VPN service encourages P2P traffic and Torrent traffic on all of their servers except those in the United States and France.
Perfect Privacy has a custom VPN manager for Windows, macOS, and Linux. Their manager supports the IPSec and OpenVPN protocols. They also have strongSwan-based IPSec client for Android which uses IKEv2. They support strong AES-256-CBC encryption. The initial handshake is by RSA-4096 with DHE. They support forward secrecy with session keys renegotiated every 60 minutes. Their service provides DNS, IPv4, and IPv6 leak protection. It also supports port forwarding, stealth VPN, and cascading servers. Finally, Perfect Privacy provides extra features like TrackStop and NeuroRouting on the server-side which can increase your security and online privacy.
What we liked about the service:
- You can create an anonymous account by paying with Bitcoin or cash.
- They do not keep individual VPN activity or connection logs logs.
- Perfect Privacy has custom software for Windows, Mac OS X, and Linux with advanced privacy features like a firewalled kill switch, DNS and IPv6 leak protection, proxy support and others.
- The service provides excellent security for both OpenVPN and IPSec connections.
- Each account has unlimited simultaneous connections.
- They allow P2P on their network servers and they have guides to help you use it more securely.
- They have server-side features like TrackStop and NeuroRouting to increase user security and privacy.
Ideas to improve the service:
- Add live chat and some form of 24/7 support.
- Develop a custom app for iOS.
- Lower the price more so more users can afford it. (Perfect Privacy is at the high end of the premium VPN services that we have reviewed which have much larger networks and some of the same features).
Perfect Privacy VPN has servers in Africa, Asia, Europe, North America, and Oceania. If privacy and anonymity are your primary reason for a VPN, their unique mix of security and privacy features could be for you. They do not offer a free trial. However, they do have a 7-day money-back guarantee for some payment methods. This means you can try out their VPN service with minimal risk. If you decide you like it you can get full access to their network from just €8.95 per month.

