At the time of this review, Golden Frog offers Cyphr apps for Android and iOS mobile devices but say apps for Windows, Mac and Internet will be coming soon. The iOS app requires iOS 7.0 or later. It is compatible with iPhone, iPad, and iPod touch and optimized for iPhone 5. The Android app requires Android 4.0.3 and up. As with their VPN service, Golden Frog owns the servers, writes the code, and manages the network to deliver all of your messages so no third party has access to them. Cyphr servers are located in Switzerland for maximum user privacy and protection.

SMS (Short Message Service) and MMS (Multimedia Messaging Service) are both used in mobile phones for non-voice communications. To understand how a secure messaging service works, first consider that when you use a regular messaging app or traditional SMS/MMS messaging, you are sending your messages to a mailbox that everyone can access which means that many people have the opportunity to read them, either by accident or for more malicious reasons. Furthermore, wi-fi packet sniffers and ISP deep packet sniffers can intercept your messages in transit and since they are not encrypted they can be read or modified without your knowledge.
Encrypted messaging services work by generating mathematical keys of the following types:
- Symmetric key – The sender and recipient have the same key.
- Public key – This is the public part of the public – private key pair.
- The recipient’s public key is used by the sender to guarantee that only the the intended recipient can access the message.
- The public key and private key are mathematically related so the sender’s pubic key can be used to verify the message sender’s identity.
- Private key – This is the private part of the public – private key pair.
- The sender can use his private key to sign the message so the recipient can verify that he sent it.
- The recipient uses his private key to open the message as it was sealed using his public key and only he can open it.
An encrypted messaging service could secure your message against all of these pitfalls by allowing you to digitally sign your message with your private key and encrypt it using the recipients public key. The service will then need to transmit the encrypted message using Secure Sockets Layer/Transport Layer Security (SSL/TLS) so that the metadata is also encrypted to the message recipient. Finally, the recipient uses their personal private key to open the message. Next they use the senders public key to verify the digital signature and decrypt the original message using their private key.
Since the message is signed and encrypted on the sender’s local machine before sending it to the recipient, all an unauthorized recipient (online sniffer or disgruntled employee) will see is a wall of text called a “hash” of the original message. Additionally, since the resultant message is transmitted using SSL/TLS the metadata is also unreadable. Finally if the message is sent to anyone other than the intended recipient they will not be able to open or read it because they do not have the private key necessary to do so. If the message is tampered with in any way then the hash will not match and the recipient will be able to tell. This ensures that the original message only reaches the intended recipient.
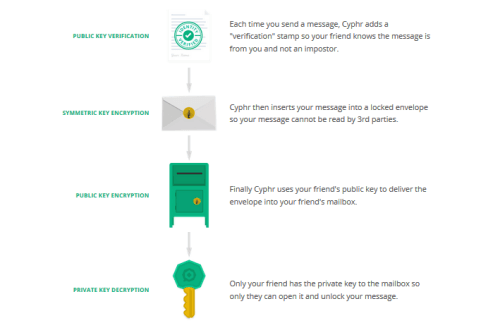
Cyphr provides an end-to-end encrypted messaging solution. A schematic of the Cyphr process as shown on their website is displayed below.
For those that have an interest, here is a more technical hi-level review of the process that their service uses. First, the message is encrypted on the sender’s device and cannot be decrypted until it reaches the recipient’s device. The steps that the sender uses to create the encrypted message as described by Cyphr follows:
- The sender creates the message he wants to send to the recipient.
- The sender signs the message with his private key so the recipient can verify that he sent the message using the sender’s public key.
- The sender creates a one-time throwaway key that is only good for this message.
- The sender encrypts both the message and the signature with the one-time key.
- The sender looks up the recipient’s public key.
- The sender encrypts the one-time key with the recipient’s public key.
- The sender signs the encrypted one-time key with the sender’s private key so the recipient knows he created it.
- The sender sends both the encrypted key and the encrypted message to the recipient via Golden Frog’s Cyphr servers.
Since all of this is done on the sender’s device, no one including Golden Frog has access to the original message until it reaches its destination and is decrypted by the intended recipient. Additionally, because the message is encrypted by a symmetric key that is encrypted by the recipient’s public key, only the recipient’s private key can access the key needed to decrypt the message. All that is stored on the Cyphr servers is the encrypted message, the message recipient, and a time-stamp showing when the message was received. It is not necessary to store any information about the sender.
In order to receive and read the message:
- The recipient downloads the encrypted key and encrypted message from the Golden Frog Cyphr servers.
- The recipient uses his private key to decrypt the encrypted symmetric key.
- The recipient uses the symmetric key to decrypt the encrypted message.
- The recipient looks up the sender’s public key.
- The recipient uses the public key to verify the message and the encrypted symmetric key were sent by the sender.
Since the private key only exists on the intended recipient’s device, only he can read the message as long as the device is secured properly. Once the message has been successfully received, the data stored for it is deleted from the Cyphr servers. The service uses the RSA algorithm for both public key encryption and verification, 256-bit AES encryption for symmetric message encryption, and TLS for secure transmission to and from the Cyphr servers which are located in Zurich, Switzerland. Cyphr is a free service and all you need to do is download the app, create an account, and generate your public and private key pair to begin using it.