Passwords have been around since ancient times. Romans used watchwords which were written on a wooden plank to exchange words which helped them identify friend and foe. The plank was exchanged from the tribune to the watch leader of the furthest camp. It then made its way back through successively closer camps to the tribune. He could examine the marks on the plank and verify that all camps had access to the watchword of the day and take appropriate measures if that was not the case. Modern military expanded on this during WWII to add not only passwords but also counter passwords. This password and response technique is commonly used by military combat units to authenticate messages from allies.

Modern passwords consists of a word or pseudo-random string of characters (upper-case and lower-case letters, symbols, and numbers) used to identity, authenticate, and provide approval to private resources. These resources could be secure computer networks, online financial institutions, or simply your personal phone or computer. Like their predecessor watchwords, they should be kept secret from those not allowed to access those resources.
A typical computer user has passwords for many purposes: logging into his many online accounts, retrieving e-mail, accessing personal mobile devices, accessing personal and business applications, databases, networks, social web sites, conducting financial business online, reading his online-newspaper, and even playing online games. It is easy to see from this list that the number of passwords that a typical user needs to remember has grown substantially over the past few years.
Bad Password Habits
Now let us examine some of the worst password habits that many users have. You should avoid all of these habits as they put your identity at risk of been hi-jacked and you could become a victim of identity theft. These include the following:
- Using the same password everywhere – this makes the user vulnerable to the “domino effect” – once a hacker steals your password from one service, he can use it on other accounts
- Rotate through a variety of similar passwords – provides similar issues as the same password – makes it easier to guess other accounts once you have a breach
- Keep a written password in a master book of passwords – this depends on how safe you keep your list
- Use personal information in a password – with all the social and research oriented websites, this makes password guessing easier
- Avoid using complicated symbols or combining upper and lower case – many are afraid they will not be able to remember them
- Never updating passwords – they feel they will not remember them if they do
- Checking the “remember me” option – this leads to many users forgetting their passwords or not being on their normal device and not remembering to sync passwords which often lead to resets and consumer frustration
- Storing passwords in the browser – browsers are not safe and require no login for the user of that machine
- Sharing passwords too liberally – many users share their passwords with family and friends
- Emailing passwords – often this results in the passwords been sent “plain text” with no encryption
- Not having a password system – this just frustrates users and makes it hard for them to keep up with the sites they have registered for often leading to password resets, 63% of users attempt to memorize passwords
So why is this important to the average user? Let us look at some startling survey statistics for those passwords that users have for their myriad of online accounts. A 2012 survey by CSIdentity found the following key findings of consumer password habits:
- 61% of users reuse passwords among multiple websites
- 78% of those age 18-24 reuse passwords – interestingly, this age group was the one most concerned with how easy the password was to remember
- only 18% have 10 or more separate passwords
- 54% of users have only five passwords or less
-
28% reported having six to 10 passwords
- only 18% have 10 or more separate passwords
-
- 35% of respondents report having security issues with their computers and passwords
- 21% of users have had an online account compromised
-
12% had personal information stolen as a result of a company security breach
- 44% of users change their password only once a year or less
- 89% of users feel secure with their current password management and use habits
Interesting enough was the fact that 73% of respondents considered strength and security as their top concern when creating passwords. Additionally, despite their risky password habits, most (89%) felt secure in their current password management habits so were unlikely to change them. This seemed to indicate a disconnect between intent and implementation when it came to password selection among survey participants.


Despite the increasing number of security breaches in the past few years, a 2014 password survey by TeleSign, a mobile verification service, showed that such habits still persist today. Their survey of over 2000 users illustrated that 62% risk online account compromise by reusing their passwords across multiple online accounts. Additionally, about 56% of survey participants had received notifications to change their passwords due to some kind of data leak in the past year. Even more disturbing, 40% of these put off changing their password and 10% never changed theirs. Among the reasons participants gave for not changing their passwords included: they would not remember new password (22%), overlooked (22%), could not be bothered (20%), and have to change them too often (16%). Equally compelling were the facts that 56% of users thought that it was the website providers responsibility for password security and that 25% of users (18-24) felt that they were safe because they had never been compromised.
These surveys show that many online password users have a false sense of security when it comes to choosing the passwords they use for their many online accounts. Additionally, others wrongly felt that they were protected by the providers of the websites that they visited. Also, the carelessness of many users, employees, and websites could ultimately impact you if you do not follow good password creation guidelines. This is illustrated by the fact that over a year after the Sony data breach, many of the same users (59% of those that had accounts on both sites) were using the same passwords on their Yahoo Voice accounts.
Those of you who think that your data is protected by the government, medical companies, and financial institutions are in for a rude awakening and many of you have already had it according to Forbes.
“In fact, a recent study found that more than 40% of companies experienced a data breach of some sort in the past year – four out of ten companies that maintain your credit card numbers, social security numbers, health information, and other personal information.”
As you can see, the combination of bad password habits and data breaches makes it imperative that you practice good password creation procedures. As long as your data is properly encrypted, your information will still be protected in the event of a data breach. This will lessen your chances of being a victim of identity theft.
How to Create Strong Passwords
Now let us look at some password creation tips that will help protect your online information. Using these practices can help ensure that if you do experience a data breach, your strong password will be one of the last to be “cracked” and may not be worth the computational resources to bother. These include the following:
- Use unique passwords for every site
- This is probably one of the most important password creation practices
- This allows you to avoid the domino effect and assure if you do have a compromised password, it will be localized to one site and protect the rest of your identity
- Use 12 characters, minimum
- This is now the minimum although 14 is better
- The longer it is, the better your password (as long as its random)
- Include numbers, symbols, capital letters, and lower-case letters
- We recommend that you use all of these in any passwords that you create
- Also more than one instance of each of these is even better
- Try to mix up how you use the above numbers, symbols, capital letters, and lower-case letters
- Do not put all of numbers at the beginning or end of your passwords – keep them random throughout the password
- Do not put all symbols at the beginning or end of your passwords – keep them random throughout the password
- Do not put all capital or lower case letters together – mix them randomly
- Is not a dictionary word or combination of dictionary words
- Avoid using real dictionary words like love, happy, good, mother, etc.
- Avoid combinations of real words like Motherof5, iloveyou, ihateyou, happywife, etc.
- Don not use personal information – names, relative’s info, pet’s name or breed, SSNs, addresses, ect.
- Doesn’t rely on obvious substitutions solely to protect your password
- Do not try to get by using short passwords and substituting say 0 for o, 3 for e, 1 for i, etc. – hackers are on to these tricks and they can make your passwords vulnerable if you rely solely on them to protect your data
- Similarly do not use words or combinations of words making such substitutions and expect this to protect you password
- Do not fill in your password hint information – if you do, make sure it is something cryptic that only you would know
- This hint information is almost always stored in “plain text” and can compromise your password no matter what other good password creation practices you use
- Being careless when filling out hints is comparable to “leaving your keys in the lock when you leave the house and inviting the burglar over” if you experience a data breech – if this seems silly to you, we agree so be careful with password hints if you use them
Ok, you have followed all of the previous practices and you have come up with three really good unique passwords for your sites:
- #klQp0cmzy%)5Hi@
- aSh39mq!(6Kle$Mm
- Wq!8*jjR1l&msCTs
These passwords fit all of the best practices: they are unique 16 characters long, completely random mixtures of numbers, symbols, capital letters, and lower-case letters. So what is the problem? Unless you are a savant with numbers, you are like most people and would probably have a problem remembering just one of these passwords, much less three. The average user now has 10+ sites they regularly visit (many with even more). Imagine trying to remember 10+ such passwords.


The problem with these passwords is that the human mind was not designed to remember long lists of random information. Memory works by association so a better way to make passwords which would be unique and easy for you to remember could be to use a phrase that only you would know. Then take only the first letter of each word along with other substitutions and other good practices and form the resultant password. To illustrate this technique, consider the phrase, “The first car I ever owned was a 1954 Ford Fairlane . I bought it for $700 from a friend!”. Taking the first letter of each word and using some substitution this becomes the following password, “Tfc1eowai954FF.ibi4$700FaF!”. This password is 27 characters long and to anyone else is a completely random series but easy for the creator to remember because it is associated with a phase only he knows.
Another method that many people have used is to use the Passphrase/Diceware method. This method has been made famous by a cartoon by the comic xkcd and is shown below.
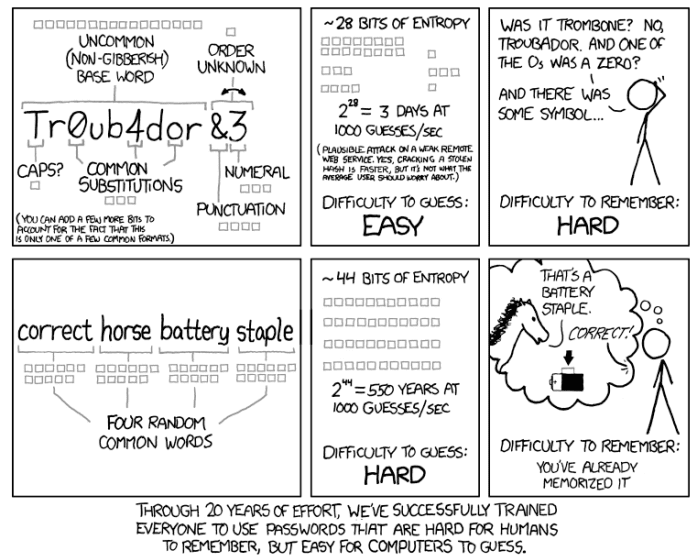

This method as illustrated by the above comic involves choosing a preferable nonsensical sentence of unrelated random words and using them as a strong password to secure your account. This method has been used for years to secure encrypted databases. The sheer length, along with the nonsensical randomness of the words makes these phrases secure. Current recommendations are that the passphrase contain at least six words to be secure against attacks by modern password crackers.
Both of the above two methods are excellent ways to create unique strong passwords to secure your personal data both locally and online. They provide all of the following benefits:
- Known only to you
- Long enough to be secure
- Hard to guess – even by someone who knows you well
- Easy for you to remember
- Easy for you to type accurately
Despite being great ways to create excellent passwords, these methods begin to lose some of their luster due to the sheer volume of passwords that today’s users must remember in their daily lives. An even better solution for most people is to employ a password manager to generate, store, and manage this sometimes overwhelming number of passwords. This leaves the user only one password to create and remember to guard his identity.
What Makes a Good Password Manager
First off, what is a password manager and how can it help you to take control of your personal and online identity? A password manager is an application which helps you create, securely store, and manage all of your passwords in one place. Password managers usually store your passwords in encrypted form and require you to use a master password to access your complete password database. We hope you remember and use the aforementioned practices and techniques to create your master password if you decide that a this is a good solution for you. This will ensure that you have a very strong password protecting your personal and online identity.
You should look at the following criteria when deciding which password manager is right for you:
- Does the software make it easy to save login information for websites while browsing the web?
- Does it make it easy to search your password database, enter, and change login information for the sites you visit?
- Does it allow you to store other kinds of information, such as credit cards, personal info, secure notes, receipts, and more so that it can help protect your complete identity?
- Does the app make it easy to sort and organize all of your personal as well as online information?
- Does it provide a means to securely share this information with others?
- Is its interface well designed and easy for you to use?
- Can it be deployed across desktop (Windows and Mac) and mobile platforms (iOS and Android)?
- Can it be securely synced or is it cloud based so that you can take advantage of it no matter what device you are currently using?
- Does it support multi-factor authentication like security token, one time passwords, and biometric input (such as a fingerprint, hand, retina, or face scanner)? – I will elaborate more on these later.
- Does it help you keep up-to-date on your security – easily allow you to see when a password was changed last?
- Can you quickly assess the strength of your passwords and generate stronger ones?
- Can you easily monitor and change passwords on a regular basis or if a breech of one of your sites is discovered?
- Does it use state-of-the art encryption standards, so in case someone gets a hold of your computer, all that sensitive information stored in your password manager is safe and secure?
Remember that your information on most websites is only as secure as the passwords you use to protect it! Though the death of the password has been predicted for many years now (Bill Gates first predicted it in 2004), we have yet to develop a method that is as convenient and easy to implement to prove your identity.
As the hardware available to those who crack passwords becomes more sophisticated this is becoming more imperative. At the end of 2012, Ars Technica reported that a 25-GPU cluster could crack every Windows password under eight characters in less than six hours using a brute force attack. As daunting as that was, according to latest incarnation of Moore’s Law
The number of transistors incorporated in a chip will approximately double every 24 months,
passwords face even greater challenges in the future. To address this more interest is being given to multi-factor authentication.
What is Multi-Factor Authentication?
Multi-factor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction. This is usually implemented using different categories of factors. In the case of computers these factors include:
- Knowledge factors- something you know
- Passwords
- Personal identification numbers (PINS),
- Secret questions
- Possession factors – something you have
- Software tokens – something presented by software on your machine that you respond too
- Hardware tokens – physical devices that the user has in his possession like one time password generators or hardware keys
- Personal (inheritance) factors – something you are
- Biometric devices – below is just a short list of such devices
- Fingerprint readers – implemented using Touch ID with an iPhone 5s or later, iPad Air 2, or iPad mini 3 or later, Microsoft readers, and implemented on some PCs
- Facial recognition – reads facial points and implemented on some laptops
- Iris identification – maps users iris to unlock device
- Voice recognition – voice verification to unlock
- Apples heartbeat monitor
- Graphics verification – requires a personal picture from user to unlock
- Biometric devices – below is just a short list of such devices
Multi-factor authentication began as visual software designed to thwart bots from disrupting websites. Gradually financial institutions started using secret questions and monitoring user habits and requiring codes sent to registered devices to access online banking if they noticed something out of the ordinary. Some institutions will allow users to request a two-step authentication process to secure their identity. Ideally the more steps used to authenticate the more secure the device or data.


The widespread adoption of smartphones coupled with an advancement in consumer biometric technology has changed the landscape of muti-stage authentication. There’s now also a stronger public and commercial will to find better authentication methods than the single password. This has been spurred by high-profile hacks (Adobe, LinkedIn, Sony, Target), which have further exposed the vulnerability of the one-time password.
The progression in muti-factor authentication is been driven by the FIDO (Fast Identity Online) Alliance and their President Michael Barrett. Their goal is to provide open specifications, so that devices and servers talk the same authentication language. FIDO’s recent progress has been impressive. It is becoming more likely that they could establish a solution by implementing authentication standards. Internet giants such as Google, Microsoft, Samsung, VISA, MasterCard, Paypal and Alipay (China’s leading online payment service) have all become FIDO members. Only time will tell if these standards will ever become widespread enough to replace the common password but it is clear that at the least such standards will make online user transactions more secure from an authentication standpoint.
Death of the Password?
First off I want to say that the death of the password had been predicted since 2004 but it is still the most efficient way that we have devised to protect our identities online. So at least for the foreseeable future, I think that most users can benefit from a good password manager as the sheer volume of passwords that they need to remember is likely to grow even larger in the future. I think that in addition, multi-factor authentication can and should be used by consumers to protect their personal and online identities. However, the practice of good password care, use, and creation is still going to be most users primary defense for keeping their online identity safe for some time to come.